How can he find the directory?
Mason is footprinting an organization to gather competitive intelligence. He visits the
company’s website for contact information and telephone numbers but does not find any. He
knows the entire staff directory was listed on their website 12 months. How can he find the
directory?
Which of the following is not a characteristic of a firewall?
Which of the following is not a characteristic of a firewall?
Identify the type of application security assessment which analyzes the application-based code to confirm̷
Application security assessment is one of the activity that a pen tester performs in the attack
phase. It is designed to identify and assess threats to the organization through bespoke,
proprietary applications or systems. It checks the application so that a malicious user cannot
access, modify, or destroy data or services within the system.
Identify the type of application security assessment which analyzes the application-based
code to confirm that it does not contain any sensitive information that an attacker might use
to exploit an application.
This value is a:
The IP protocol was designed for use on a wide variety of transmission links. Although the
maximum length of an IP datagram is 64K, most transmission links enforce a smaller
maximum packet length limit, called a MTU. The value of the MTU depends on the type of
the transmission link. The design of IP accommodates MTU differences by allowing routers
to fragment IP datagrams as necessary. The receiving station is responsible for
reassembling the fragments back into the original full size IP datagram. IP fragmentation
involves breaking a datagram into a number of pieces that can be reassembled later. The IP
source, destination, identification, total length, and fragment offset fields in the IP header,
are used for IP fragmentation and reassembly.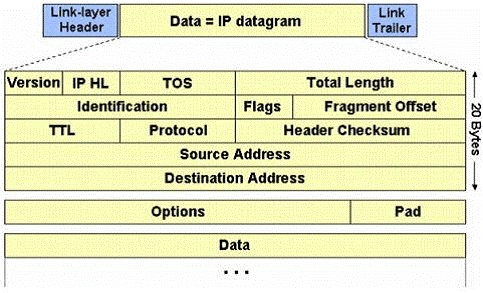
The fragment offset is 13 bits and indicates where a fragment belongs in the original IP
datagram. This value is a:
where can clues about the underlying application environment can be collected?
From where can clues about the underlying application environment can be collected?
Which of the following information gathering techniques collects information from an organization’s web-base
Which of the following information gathering techniques collects information from an
organization’s web-based calendar and email services?
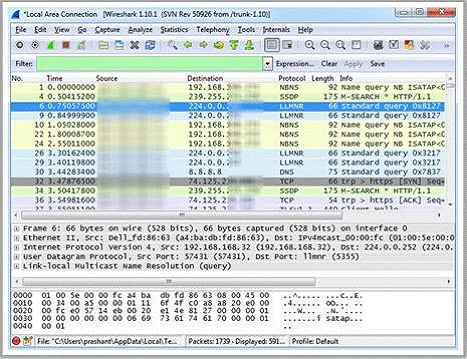
Which Wireshark filter displays all the packets where the IP address of the source host is 10.0.0.7?
Which of the following statements is true about the LM hash?
Which of the following statements is true about the LM hash?
Which of the following statement holds true for TCP Operation?
Which of the following will not handle routing protocols properly?
Which of the following will not handle routing protocols properly?