Which of the following is not a condition specified by Hamel and Prahalad (1990)?
Which of the following is not a condition specified by Hamel and Prahalad (1990)?
Which of the following information gathering terminologies refers to gathering information through social engi
The first and foremost step for a penetration test is information gathering. The main objective
of this test is to gather information about the target system which can be used in a malicious
manner to gain access to the target systems.
Which of the following information gathering terminologies refers to gathering information
through social engineering on-site visits, face-to-face interviews, and direct questionnaires?
Which of the following flaws refers to an application using poorly written encryption code to securely encrypt
Today, most organizations would agree that their most valuable IT assets reside within
applications and databases. Most would probably also agree that these are areas that have
the weakest levels of security, thus making them the prime target for malicious activity from
system administrators, DBAs, contractors, consultants, partners, and customers.
Which of the following flaws refers to an application using poorly written encryption code to
securely encrypt and store sensitive data in the database and allows an attacker to steal or
modify weakly protected data such as credit card numbers, SSNs, and other authentication
credentials?
What type of DoS attack is James testing against his network?
James is testing the ability of his routers to withstand DoS attacks. James sends ICMP
ECHO requests to the broadcast address of his network. What type of DoS attack is James
testing against his network?
which of the following IDS evasion techniques does IDS reject the packets that an end system accepts?
In which of the following IDS evasion techniques does IDS reject the packets that an end
system accepts?
Which of the following attacks does a hacker perform in order to obtain UDDI information such as business Enti
Which of the following attacks does a hacker perform in order to obtain UDDI information
such as business Entity, busines Service, binding Template, and tModel?
DNS information records provide important data about:
DNS information records provide important data about:
Which of the following is NOT a pen testing component to be tested?
The first phase of the penetration testing plan is to develop the scope of the project in
consultation with the client. Pen testing test components depend on the client’s operating
environment, threat perception, security and compliance requirements, ROE, and budget.
Various components need to be considered for testing while developing the scope of the project.
Which of the following is NOT a pen testing component to be tested?
which of the following locations?
Windows stores user passwords in the Security Accounts Manager database (SAM), or in
the Active Directory database in domains. Passwords are never stored in clear text;
passwords are hashed and the results are stored in the SAM.
NTLM and LM authentication protocols are used to securely store a user’s password in the
SAM database using different hashing methods.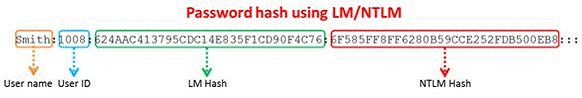
The SAM file in Windows Server 2008 is located in which of the following locations?
which of the following?
A firewall’s decision to forward or reject traffic in network filtering is dependent upon which of
the following?

