Which NMAP switch would the hacker use?
A hacker is attempting to see which IP addresses are currently active on a network. Which NMAP switch would
the hacker use?
Which of the following open source tools would be the b…
Which of the following open source tools would be the best choice to scan a network for potential targets?
Which of the following parameters enables NMAP’s operat…
Which of the following parameters enables NMAP’s operating system detection feature?
What results will the following command yield: ‘NMAP -s…
What results will the following command yield: ‘NMAP -sS -O -p 123-153 192.168.100.3’?
Which command lets a tester enumerate alive systems in …
Which command lets a tester enumerate alive systems in a class C network via ICMP using native Windows
tools?
Which solution can be used to emulate computer services…
Which solution can be used to emulate computer services, such as mail and ftp, and to capture information
related to logins or actions?
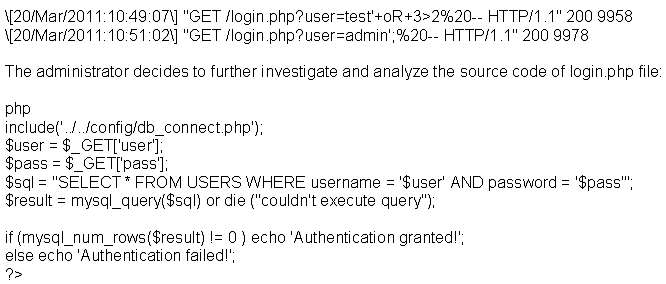
A security administrator notices that the log file of t…
Which web applications vulnerability did the analyst di…
A security analyst in an insurance company is assigned to test a new web application that will be used by clients
to help them choose and apply for an insurance plan. The analyst discovers that the application is developed in
ASP scripting language and it uses MSSQL as a database backend. The analyst locates the application’s
search form and introduces the following code in the search input field:
IMG SRC=vbscript:msgbox(“Vulnerable”);> originalAttribute=”SRC” originalPath=”vbscript:msgbox
(“Vulnerable”);>”
When the analyst submits the form, the browser returns a pop-up window that says “Vulnerable”.
Which web applications vulnerability did the analyst discover?
What pseudo code would the developer use to avoid a buf…
A developer for a company is tasked with creating a program that will allow customers to update their billing and
shipping information. The billing address field used is limited to 50 characters. What pseudo code would the
developer use to avoid a buffer overflow attack on the billing address field?
What statement is true regarding LM hashes?
What statement is true regarding LM hashes?