A program that defends against a port scanner will attempt to:
A program that defends against a port scanner will attempt to:
Which of the following is the best remediation against this type of attack?
A network security administrator is worried about potential man-in-the-middle attacks when users
access a corporate web site from their workstations. Which of the following is the best remediation
against this type of attack?
what do you infer from the attack?
Which command line switch would be used in NMAP to perform operating system detection?
Which command line switch would be used in NMAP to perform operating system detection?
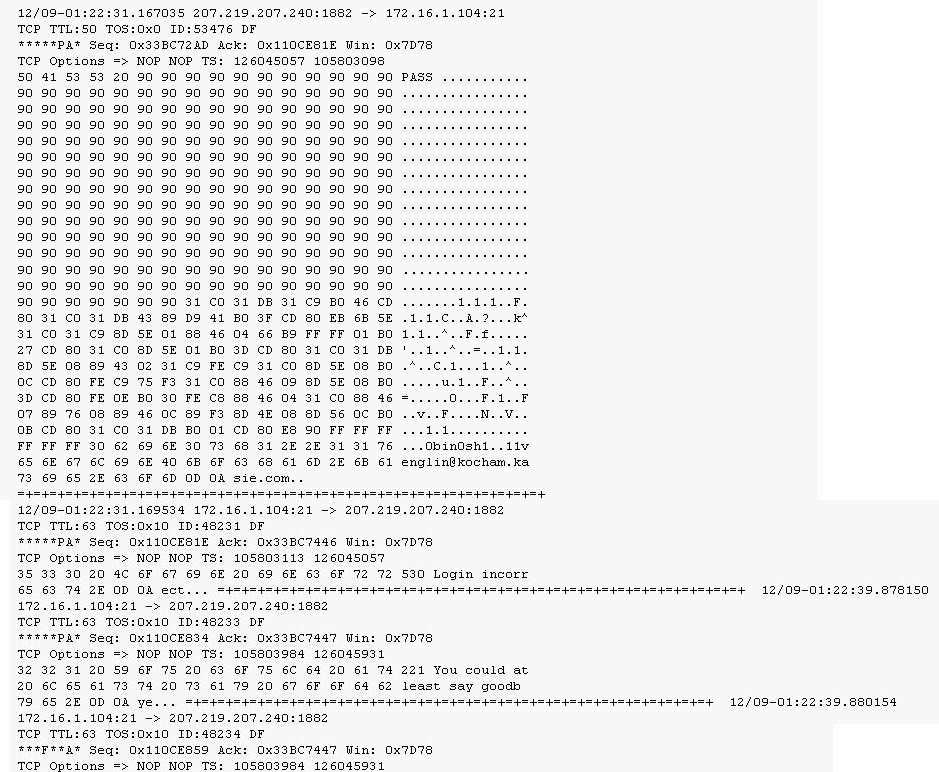
what service is being exploited?
Exhibit:
Given the following extract from the snort log on a honeypot, what service is being exploited? :
which digital modulation technique to exchange information between paired devices?
Bluetooth uses which digital modulation technique to exchange information between paired
devices?
Which of these describes a low interaction honeypot?
There are two types of honeypots- high and low interaction. Which of these describes a low
interaction honeypot? Select the best answers.
which kind of attack?
A security consultant decides to use multiple layers of anti-virus defense, such as end user
desktop anti-virus and E-mail gateway. This approach can be used to mitigate which kind of
attack?
What tool might he use to bypass the IDS?
An Evil Cracker is attempting to penetrate your private network security. To do this, he must not be
seen by your IDS, as it may take action to stop him. What tool might he use to bypass the IDS?
Select the best answer.
A security policy will be more accepted by employees if it is consistent and has the support of
A security policy will be more accepted by employees if it is consistent and has the support of