Which of the statements concerning proxy firewalls is correct?
Which of the statements concerning proxy firewalls is correct?
What do you recommend?
Peter is a Linux network admin. As a knowledgeable security consultant, he turns to you to look for
help on a firewall. He wants to use Linux as his firewall and use the latest freely available version
that is offered. What do you recommend?
Select the best answer.
Which of the following is an example of two factor authentication?
Which of the following is an example of two factor authentication?
which among the following would be appropriate?
Which of the following is likely to occur as a result?
A security consultant is trying to bid on a large contract that involves penetration testing and
reporting. The company accepting bids wants proof of work so the consultant prints out several
audits that have been performed. Which of the following is likely to occur as a result?
What is this process known as?
You are attempting to map out the firewall policy for an organization. You discover your target
system is one hop beyond the firewall. Using hping2, you send SYN packets with the exact TTL of
the target system starting at port 1 and going up to port 1024. What is this process known as?
which of the following is likely to be installed on the target machine by the OS?
A penetration tester is conducting a port scan on a specific host. The tester found several ports
opened that were confusing in concluding the Operating System (OS) version installed.
Considering the NMAP result below, which of the following is likely to be installed on the target
machine by the OS?
Starting NMAP 5.21 at 2011-03-15 11:06
NMAP scan report for 172.16.40.65
Host is up (1.00s latency).
Not shown: 993 closed ports
PORT STATE SERVICE
21/tcp open ftp
23/tcp open telnet
80/tcp open http
139/tcp open netbios-ssn
515/tcp open
631/tcp open ipp
9100/tcp open
MAC Address: 00:00:48:0D:EE:89
What would be the best countermeasure to protect against escalation of priveges?
Once an intruder has gained access to a remote system with a valid username and password, the
attacker will attempt to increase his privileges by escalating the used account to one that has
increased privileges. such as that of an administrator. What would be the best countermeasure to
protect against escalation of priveges?
What is the outcome of the comm”nc -l -p 2222 | nc 10.1.0.43 1234"?
What is the outcome of the comm”nc -l -p 2222 | nc 10.1.0.43 1234″?
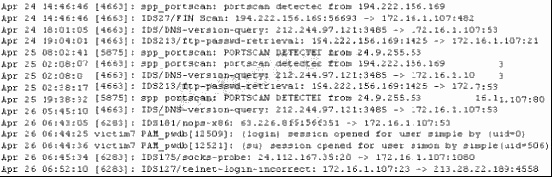
Which one of the following attacks will pass through a network layer intrusion detection system undetected?
Which one of the following attacks will pass through a network layer intrusion detection system
undetected?