Choose the attack type from the choices given below.
Bill is attempting a series of SQL queries in order to map out the tables within the database that he
is trying to exploit.
Choose the attack type from the choices given below.
which of the following commands will start the Nessus client in the background so that the Nessus server can b
On a Linux device, which of the following commands will start the Nessus client in the background
so that the Nessus server can be configured?
What is the next step you should do?
Least privilege is a security concept that requires that a user is
Least privilege is a security concept that requires that a user is
What would you call such an attack?
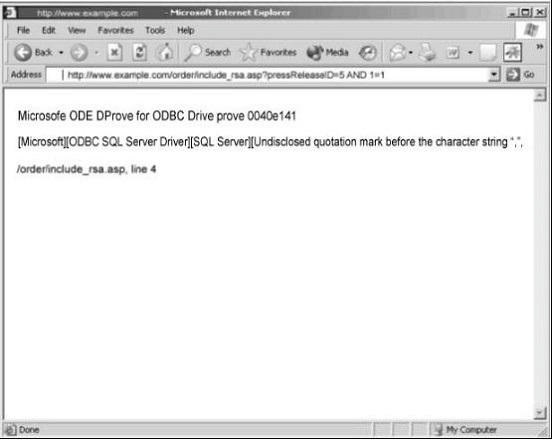
Your boss Tess King is attempting to modify the parameters of a Web-based application in order
to alter the SQL statements that are parsed to retrieve data from the database. What would you
call such an attack?
A covert channel is a channel that
A covert channel is a channel that
what would be among the first steps that he would perform?
When a malicious hacker identifies a target and wants to eventually compromise this target, what
would be among the first steps that he would perform? (Choose the best answer)
which technology to format information?
SOAP services use which technology to format information?
How would an attacker use this technique to compromise a database?
A particular database threat utilizes a SQL injection technique to penetrate a target system. How
would an attacker use this technique to compromise a database?
What type of scan is this?
A security engineer is attempting to map a company’s internal network. The engineer enters in the
following NMAP commanD.
NMAP –n –sS –P0 –p 80 ***.***.**.**
What type of scan is this?