Who is considered an insider?
A majority of attacks come from insiders, people who have direct access to a company’s computer
system as part of their job function or a business relationship. Who is considered an insider?
What would be the best method to accurately identify the services running on a victim host?
Scanning for services is an easy job for Bob as there are so many tools available from the
Internet. In order for him to check the vulnerability of XYZ, he went through a few scanners that
are currently available. Here are the scanners that he uses:
1. Axent’s NetRecon (http://www.axent.com)
2. SARA, by Advanced Research Organization (http://www-arc.com/sara)
3. VLAD the Scanner, by Razor (http://razor.bindview.com/tools/)
However, there are many other alternative ways to make sure that the services that have been
scanned will be more accurate and detailed for Bob.
What would be the best method to accurately identify the services running on a victim host?
What will the SQL statement accomplish?
Jeremy is web security consultant for Information Securitas. Jeremy has just been hired to perform
contract work for a large state agency in Michigan. Jeremy’s first task is to scan all the company’s
external websites. Jeremy comes upon a login page which appears to allow employees access to
sensitive areas on the website. James types in the following statement in the username field:
SELECT * from Users where username=’admin’ ?AND password=” AND email like
‘%@testers.com%’
What will the SQL statement accomplish?
Why is Jim having these problems?
Jim is having no luck performing a penetration test in XYZ’s network. He is running the tests from
home and has downloaded every security scanner that he could lay his hands on. Despite
knowing the IP range of all the systems, and the exact network configuration, Jim is unable to get
any useful results.
Why is Jim having these problems?
What could be the reason?
An attacker is attempting to telnet into a corporation’s system in the DMZ. The attacker doesn’t
want to get caught and is spoofing his IP address. After numerous tries he remains unsuccessful
in connecting to the system. The attacker rechecks that the target system is actually listening on
Port 23 and he verifies it with both nmap and hping2. He is still unable to connect to the target
system. What could be the reason?
What kind of assessment will you be performing ?
You have just received an assignment for an assessment at a company site. Company’s
management is concerned about external threat and wants to take appropriate steps to insure
security is in place. Anyway the management is also worried about possible threats coming from
inside the site, specifically from employees belonging to different Departments. What kind of
assessment will you be performing ?
what will be the response?
If an attacker’s computer sends an IPID of 31400 to a zombie (Idle Scanning) computer on an
open port, what will be the response?
What does black box testing mean?
What does black box testing mean?
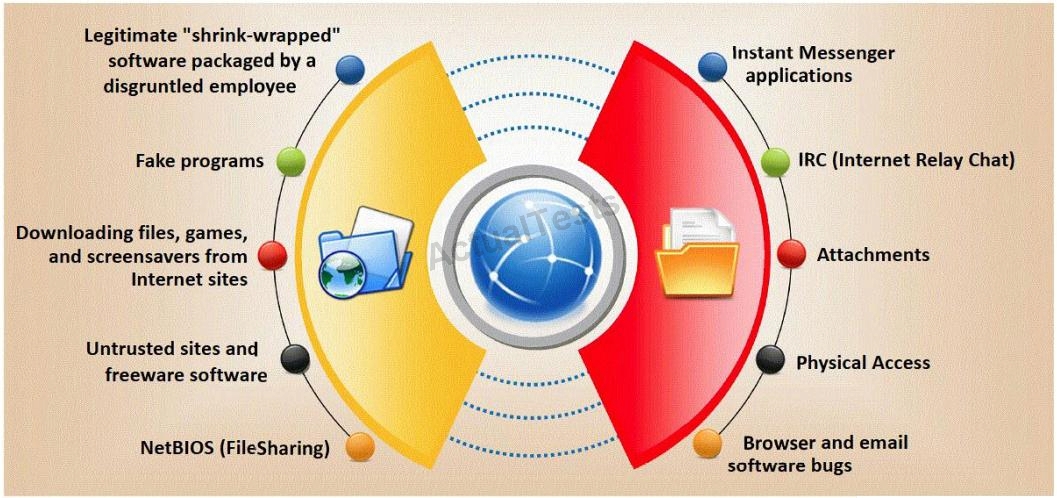
Which are the easiest and most convincing ways to infect a computer?
What do you think has occurred?
Bryan notices the error on the web page and asks Liza to enter liza’ or ‘1’=’1 in the email field.
They are greeted with a message “Your login information has been mailed to
johndoe@gmail.com”. What do you think has occurred?