What would you term this attack?
Kevin sends an email invite to Chris to visit a forum for security professionals. Chris clicks on the
link in the email message and is taken to a web based bulletin board. Unknown to Chris, certain
functions are executed on his local system under his privileges, which allow Kevin access to
information used on the BBS. However, no executables are downloaded and run on the local
system. What would you term this attack?
Why does the host respond to hping2 and not ping packet?
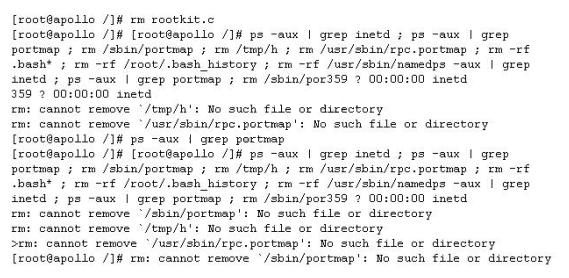
What is the probable cause of Bill’s problem?
Bill has successfully executed a buffer overflow against a Windows IIS web server. He has been
able to spawn an interactive shell and plans to deface the main web page. He first attempts to use
the “echo” command to simply overwrite index.html and remains unsuccessful. He then attempts
to delete the page and achieves no progress. Finally, he tries to overwrite it with another page in
which also he remains unsuccessful. What is the probable cause of Bill’s problem?
What is the hacker trying to accomplish here?
Which of the following statements best describes the term Vulnerability?
Which of the following statements best describes the term Vulnerability?
What has Blake just accomplished?
Blake is in charge of securing all 20 of his company’s servers. He has enabled hardware and
software firewalls, hardened the operating systems, and disabled all unnecessary services on all
the servers. Unfortunately, there is proprietary AS400 emulation software that must run on one of
the servers that requires the telnet service to function properly. Blake is especially concerned
about this since telnet can be a very large security risk in an organization. Blake is concerned
about how this particular server might look to an outside attacker so he decides to perform some
footprinting, scanning, and penetration tests on the server. Blake telnets into the server using Port
80 and types in the following command:
HEAD / HTTP/1.0
After pressing enter twice, Blake gets the following results: What has Blake just accomplished?
Which of the following web browser can adequately fill this purpose?
Bob is a very security conscious computer user. He plans to test a site that is known to have
malicious applets, code, and more. Bob always make use of a basic Web Browser to perform such
testing.
Which of the following web browser can adequately fill this purpose?
What must be enabled in SQL Server to launch these attacks?
You want to perform advanced SQL Injection attack against a vulnerable website. You are unable
to perform command shell hacks on this server. What must be enabled in SQL Server to launch
these attacks?
How much information will Clive obtain from the client before commencing his test?
Clive has been hired to perform a Black-Box test by one of his clients.
How much information will Clive obtain from the client before commencing his test?
What is Kevin attempting hereto gain access to Katy’s mailbox?
Kevin is an IT security analyst working for Emerson Time Makers, a watch manufacturing
company in Miami. Kevin and his girlfriend Katy recently broke up after a big fight. Kevin believes
that she was seeing another person. Kevin, who has an online email account that he uses for most
of his mail, knows that Katy has an account with that same company. Kevin logs into his email
account online and gets the following URL after successfully logged in:
http://www.youremailhere.com/mail.asp?mailbox=Kevin&Smith=121%22 Kevin changes the URL
to: http://www.youremailhere.com/mail.asp?mailbox=Katy&Sanchez=121%22 Kevin is trying to
access her email account to see if he can find out any information. What is Kevin attempting here
to gain access to Katy’s mailbox?