Why did the 14 character passwords not take much longer to crack than the 8 character passwords?
Harold works for Jacobson Unlimited in the IT department as the security manager. Harold has
created a security policy requiring all employees to use complex 14 character passwords.
Unfortunately, the members of management do not want to have to use such long complicated
passwords so they tell Harold’s boss this new password policy should not apply to them. To
comply with the management’s wishes, the IT department creates another Windows domain and
moves all the management users to that domain. This new domain has a password policy only
requiring 8 characters.
Harold is concerned about having to accommodate the managers, but cannot do anything about it.
Harold is also concerned about using LanManager security on his network instead of NTLM or
NTLMv2, but the many legacy applications on the network prevent using the more secure NTLM
and NTLMv2. Harold pulls the SAM files from the DC’s on the original domain and the new domain
using Pwdump6.
Harold uses the password cracking software John the Ripper to crack users’ passwords to make
sure they are strong enough. Harold expects that the users’ passwords in the original domain will
take much longer to crack than the management’s passwords in the new domain. After running the
software, Harold discovers that the 14 character passwords only took a short time longer to crack
than the 8 character passwords.
Why did the 14 character passwords not take much longer to crack than the 8 character
passwords?
What encryption algorithm will you be decrypting?
You are attempting to crack LM Manager hashed from Windows 2000 SAM file. You will be using
LM Brute force hacking tool for decryption.
What encryption algorithm will you be decrypting?
-DNS query is sent to the DNS server to resolve www.google.com -DNS server replies with the IP address for Goo
You establish a new Web browser connection to Google. Since a 3-way handshake is required for
any TCP connection, the following actions will take place.
-DNS query is sent to the DNS server to resolve www.google.com
-DNS server replies with the IP address for Google?
-SYN packet is sent to Google.
-Google sends back a SYN/ACK packet
-Your computer completes the handshake by sending an ACK
-The connection is established and the transfer of data commences
Which of the following packets represent completion of the 3-way handshake?
what would you call such an attack?
In the context of password security, a simple dictionary attack involves loading a dictionary file (a
text file full of dictionary words) into a cracking application such as L0phtCrack or John the Ripper,
and running it against user accounts located by the application. The larger the word and word
fragment selection, the more effective the dictionary attack is. The brute force method is the most
inclusive, although slow. It usually tries every possible letter and number combination in its
automated exploration.
If you would use both brute force and dictionary methods combined together to have variation of
words, what would you call such an attack?
which you will NOT be able to accomplish with this probe?
What is the algorithm used by LM for Windows2000 SAM?
What is the algorithm used by LM for Windows2000 SAM?
Which of the following Trojans would be considered ‘Botnet Command Control Center’?
Which of the following Trojans would be considered ‘Botnet Command Control Center’?
which of the following?
E-mail scams and mail fraud are regulated by which of the following?
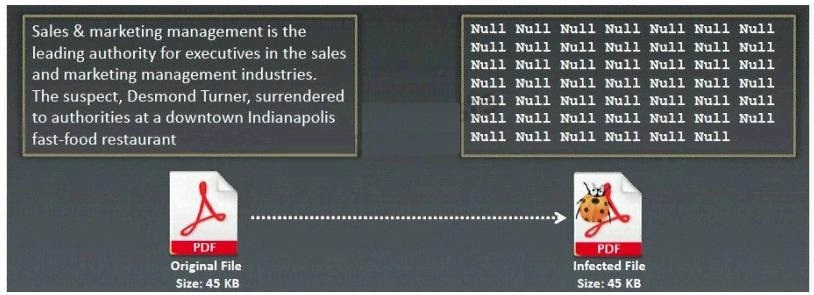
What type of Virus is shown here?
Which of the following LM hashes represent a password of less than 8 characters?
Which of the following LM hashes represent a password of less than 8 characters? (Select 2)