Which TCP and UDP ports must you filter to check null sessions on your network?
Null sessions are un-authenticated connections (not using a username or password.) to an NT or
2000 system. Which TCP and UDP ports must you filter to check null sessions on your network?
What framework architecture is shown in this exhibit?
Study the following log extract and identify the attack.
Which of the following steganography utilities exploits the nature of white space and allows the user to conce
Which of the following steganography utilities exploits the nature of white space and allows the
user to conceal information in these white spaces?
what is the hacker really trying to steal?
Exhibit:
Based on the following extract from the log of a compromised machine, what is the hacker really
trying to steal?
How long will it take to crack the password by an attacker?
You have chosen a 22 character word from the dictionary as your password. How long will it take
to crack the password by an attacker?
what would you conclude about the attack?
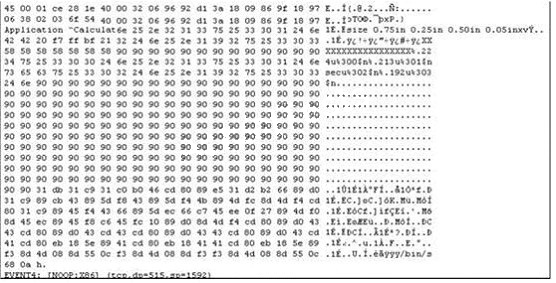
The following is an entry captured by a network IDS.You are assigned the task of analyzing this
entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel
processor. You figure that the attacker is attempting a buffer overflow attack. You also notice
“/bin/sh” in the ASCII part of the output. As an analyst what would you conclude about the attack?
What vulnerability is detected in the web application here?
While testing web applications, you attempt to insert the following test script into the search area
on the company’s web site:
<script>alert(‘Testing Testing Testing’)</script>
Later, when you press the search button, a pop up box appears on your screen with the text
“Testing Testing Testing”. What vulnerability is detected in the web application here?
what are some of the things you would recommend to a company to ensure DNS security?
As a securing consultant, what are some of the things you would recommend to a company to
ensure DNS security? Select the best answers.
What techniques would you use to evade IDS during a Port Scan?
What techniques would you use to evade IDS during a Port Scan? (Select 4 answers)