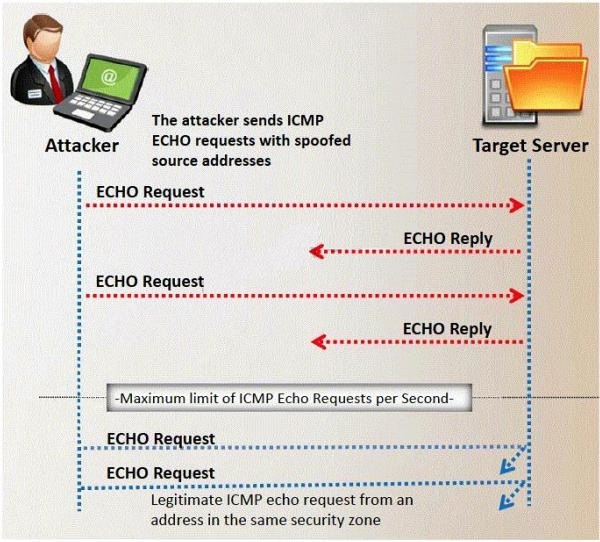
Choose one of the following pseudo codes to describe this statement…
Choose one of the following pseudo codes to describe this statement:
“If we have written 200 characters to the buffer variable, the stack should stop because it cannot
hold any more data.”
Which statement correctly defines this term?
One of the effective DoS/DDoS countermeasures is ‘Throttling’. Which statement correctly defines
this term?
Which of the following tools can be used to perform a zone transfer?
Which of the following tools can be used to perform a zone transfer?
Which of the below Google search string brings up sites with "config.php" files?
Attackers footprint target Websites using Google Hacking techniques. Google hacking is a term
that refers to the art of creating complex search engine queries. It detects websites that are
vulnerable to numerous exploits and vulnerabilities. Google operators are used to locate specific
strings of text within the search results.
The configuration file contains both a username and a password for an SQL database. Most sites
with forums run a PHP message base. This file gives you the keys to that forum, including FULL
ADMIN access to the database. WordPress uses config.php that stores the database Username
and Password.
Which of the below Google search string brings up sites with “config.php” files?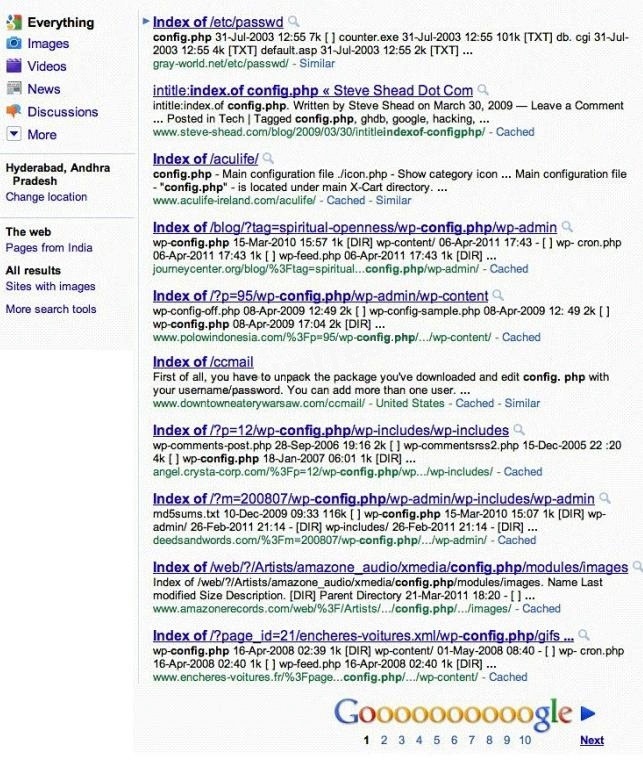
what conditions does a secondary name server request a zone transfer from a primary name server?
Under what conditions does a secondary name server request a zone transfer from a primary
name server?
Which of the following tool would be considered as Signature Integrity Verifier (SIV)?
Which of the following tool would be considered as Signature Integrity Verifier (SIV)?
What ports should be blocked on the firewall to prevent NetBIOS traffic from not coming through the firewall i
What ports should be blocked on the firewall to prevent NetBIOS traffic from not coming through
the firewall if your network is comprised of Windows NT, 2000, and XP?(Choose all that apply.
Why will this not be possible?
Bob has set up three web servers on Windows Server 2008 IIS 7.0. Bob has followed all the
recommendations for securing the operating system and IIS. These servers are going to run
numerous e-commerce websites that are projected to bring in thousands of dollars a day. Bob is
still concerned about the security of these servers because of the potential for financial loss. Bob
has asked his company’s firewall administrator to set the firewall to inspect all incoming traffic on
ports 80 and 443 to ensure that no malicious data is getting into the network.
Why will this not be possible?
What is a NULL scan?
What is a NULL scan?