What is the following command used for?
What is the following command used for?
net use \targetipc$ “” /u:””
Which of the following is NOT an example of default installation?
Attacking well-known system defaults is one of the most common hacker attacks. Most software is
shipped with a default configuration that makes it easy to install and setup the application. You
should change the default settings to secure the system.
Which of the following is NOT an example of default installation?
What is the proper response for a NULL scan if the port is closed?
What is the proper response for a NULL scan if the port is closed?
What is the most efficient way an attacker located in remote location to infect this banking Trojan on a victi
BankerFox is a Trojan that is designed to steal users’ banking data related to certain banking
entities.
When they access any website of the affected banks through the vulnerable Firefox 3.5 browser,
the Trojan is activated and logs the information entered by the user. All the information entered in
that website will be logged by the Trojan and transmitted to the attacker’s machine using covert
channel.
BankerFox does not spread automatically using its own means. It needs an attacking user’s
intervention in order to reach the affected computer.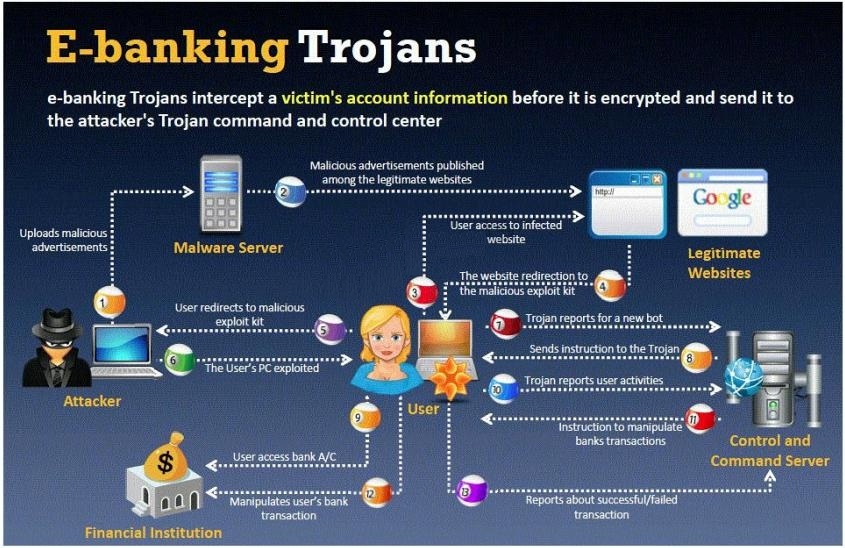
What is the most efficient way an attacker located in remote location to infect this banking Trojan
on a victim’s machine?
Name the tool is widely used for ARP Poisoning attack?
What is the TTL?
One of your team members has asked you to analyze the following SOA record. What is the TTL?
Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600
3600 604800 2400.
what would you call such an attack?
In the context of password security: a simple dictionary attack involves loading a dictionary file (a
text file full of dictionary words) into a cracking application such as L0phtCrack or John the Ripper,
and running it against user accounts located by the application. The larger the word and word
fragment selection, the more effective the dictionary attack is. The brute force method is the most
inclusive – though slow. Usually, it tries every possible letter and number combination in its
automated exploration. If you would use both brute force and dictionary combined together to have
variations of words, what would you call such an attack?
What is the version?
One of your team members has asked you to analyze the following SOA record. What is the
version?
Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600
3600 604800 2400.
What category of virus is this?
You receive an e-mail with the following text message.
“Microsoft and HP today warned all customers that a new, highly dangerous virus has been
discovered which will erase all your files at midnight. If there’s a file called hidserv.exe on your
computer, you have been infected and your computer is now running a hidden server that allows
hackers to access your computer. Delete the file immediately. Please also pass this message to
all your friends and colleagues as soon as possible.”
You launch your antivirus software and scan the suspicious looking file hidserv.exe located in
c:\windows directory and the AV comes out clean meaning the file is not infected. You view the file
signature and confirm that it is a legitimate Windows system file “Human Interface Device
Service”.
What category of virus is this?
(True/False.
MX record priority increases as the number increases. (True/False.


