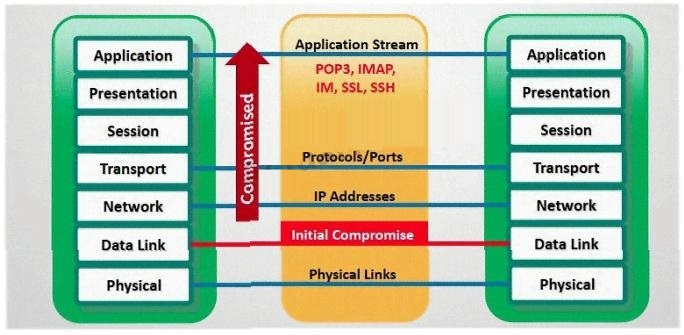
which part of OSI layer, ARP Poisoning occurs?
What ICMP message types are used by the ping command?
What ICMP message types are used by the ping command?
How will you accomplish this?
You want to hide a secret.txt document inside c:\windows\system32\tcpip.dll kernel library using
ADS streams. How will you accomplish this?
Which of the following systems would not respond correctly to an nmap XMAS scan?
Which of the following systems would not respond correctly to an nmap XMAS scan?
Windows is dangerously insecure when unpacked from the box, and there are a few things that you must do before
You just purchased the latest DELL computer, which comes pre-installed with Windows 7,
McAfee antivirus software and a host of other applications. You want to connect Ethernet wire to
your cable modem and start using the computer immediately. Windows is dangerously insecure
when unpacked from the box, and there are a few things that you must do before you use it.
Use the traceroute results shown above to answer the following question: The perimeter security at targetcor
what is the definition of a Wrapper?
In the context of Trojans, what is the definition of a Wrapper?
What should be your next step to identify the OS?
While attempting to discover the remote operating system on the target computer, you receive the
following results from an nmap scan:
Remote operating system guess: Too many signatures match to reliably guess the OS.
Nmap run completed — 1 IP address (1 host up) scanned in 277.483 seconds
What should be your next step to identify the OS?
Which step would you perform to detect this type of Trojan?
which of the following sets of requests does it send to the target device?
When Nmap performs a ping sweep, which of the following sets of requests does it send to the
target device?