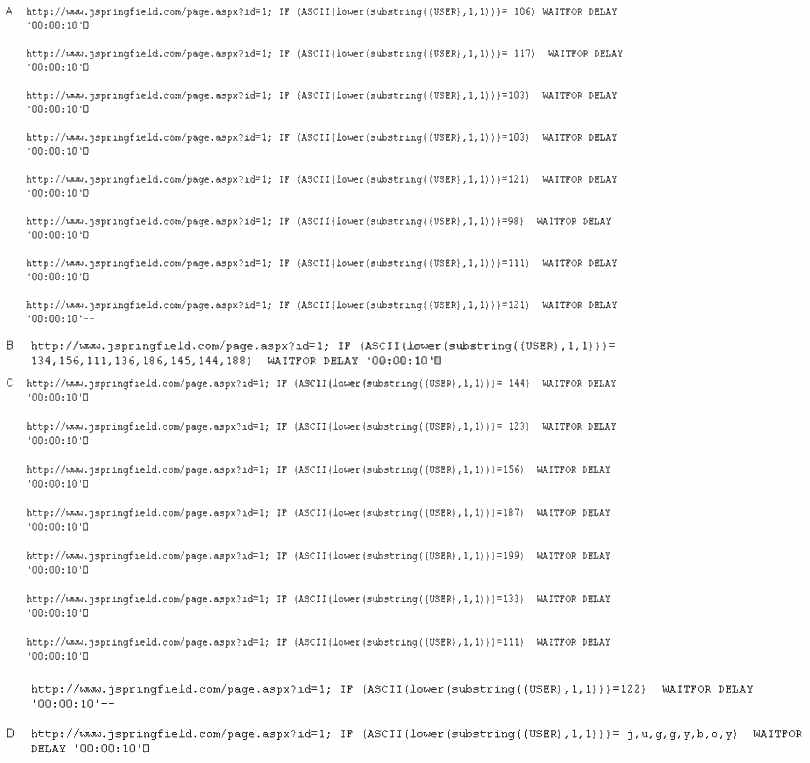
Which of the following command results in packets that will appear to originate from the system at 10.8.8.8?
Perimeter testing means determining exactly what your firewall blocks and what it allows. To
conduct a good test, you can spoof source IP addresses and source ports. Which of the following
command results in packets that will appear to originate from the system at 10.8.8.8? Such a
packet is useful for determining whether the firewall is allowing random packets in or out of your
network.
The URL may appear like this: https://www.xsecurity-bank.com/creditcard.asp?
The GET method should never be used when sensitive data such as credit card is being sent to a
CGI program. This is because any GET command will appear in the URL, and will be logged by
any servers. For example, let’s say that you’ve entered your credit card information into a form that
uses the GET method. The URL may appear like this:
https://www.xsecurity-bank.com/creditcard.asp?cardnumber=453453433532234
The GET method appends the credit card number to the URL. This means that anyone with
access to a server log will be able to obtain this information. How would you protect from this type
of attack?
How will you defend against hardware keyloggers when using public computers and Internet Kiosks?
Keystroke logging is the action of tracking (or logging) the keys struck on a keyboard, typically in a
covert manner so that the person using the keyboard is unaware that their actions are being monitored.

How will you defend against hardware keyloggers when using public computers and Internet Kiosks? (Select 4 answers)
Why did this ping sweep only produce a few responses?
Lauren is performing a network audit for her entire company. The entire network is comprised of
around 500 computers. Lauren starts an ICMP ping sweep by sending one IP packet to the
broadcast address of the network, but only receives responses from around five hosts. Why did
this ping sweep only produce a few responses?
What can Wayne infer from this traffic log?
Wayne is the senior security analyst for his company. Wayne is examining some traffic logs on a
server and came across some inconsistencies. Wayne finds some IP packets from a computer
purporting to be on the internal network. The packets originate from 192.168.12.35 with a TTL of
15. The server replied to this computer and received a response from 192.168.12.35 with a TTL of
21. What can Wayne infer from this traffic log?
What type of port scan is shown below?
What is the correct syntax?
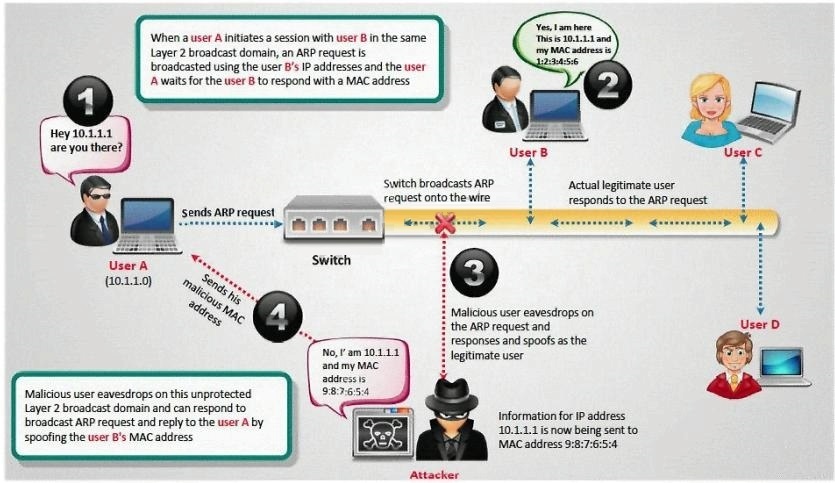
How do you defend against ARP Poisoning attack?
How can you achieve this?
You are the security administrator for a large network. You want to prevent attackers from running
any sort of traceroute into your DMZ and discovering the internal structure of publicly accessible
areas of the network. How can you achieve this?
What type of social engineering attack has Neil employed here?
Neil is an IT security consultant working on contract for Davidson Avionics. Neil has been hired to
audit the network of Davidson Avionics. He has been given permission to perform any tests
necessary. Neil has created a fake company ID badge and uniform. Neil waits by one of the
company’s entrance doors and follows an employee into the office after they use their valid access
card to gain entrance. What type of social engineering attack has Neil employed here?