Which of the following refers to the exploitation of a valid computer session to gain unauthorized access to i
Which of the following refers to the exploitation of a valid computer session to gain unauthorized
access to information or services in a computer system?
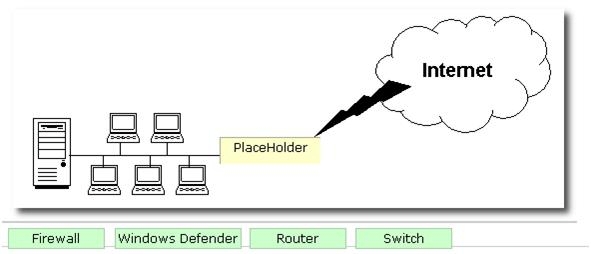
What will George use to protect the network of the company from intrusion?
Which of the following are the common security problems involved in communications and email?
Which of the following are the common security problems involved in communications and
email?Each correct answer represents a complete solution. Choose all that apply.
Which of the following layers of TCP/IP model is used to move packets between the Internet Layer interfaces of
Which of the following layers of TCP/IP model is used to move packets between the Internet Layer
interfaces of two different hosts on the same link?
__________ is the process, policies, and procedures related to preparing for recovery or continuation of techn
CORRECT TEXT
Fill in the blank with the appropriate term. ________________ is the process, policies, and
procedures related to preparing for recovery or continuation of technology infrastructure critical to
an organization after a natural or human-induced disaster.
Which of the following is most appropriate for this client?
You are advising a school district on disaster recovery plans. In case a disaster affects the main IT
centers for the district they will need to be able to work from an alternate location. However,
budget is an issue. Which of the following is most appropriate for this client?
Which of the following techniques uses a modem in order to automatically scan a list of telephone numbers?
Which of the following techniques uses a modem in order to automatically scan a list of telephone
numbers?
Alternate Data Streams (ADS) is a feature of the______________ file system, allowing more than one data stream
CORRECT TEXT
Fill in the blank with the appropriate file system. Alternate Data Streams (ADS) is a feature of
the______________ file system, allowing more than one data stream to be associated with a
filename.
Which of the following policies is used to add additional information about the overall security posture…
Which of the following policies is used to add additional information about the overall security
posture and serves to protect employees and organizations from inefficiency or ambiguity?
Which of the following statements best describes the consequences of the disaster recovery plan test?
Which of the following statements best describes the consequences of the disaster recovery plan
test?