Which of the following policies is used to add additional information about the overall security posture…
Which of the following policies is used to add additional information about the overall security
posture and serves to protect employees and organizations from inefficiency or ambiguity?
Which of the following tools is John using to crack the wireless encryption keys?
John works as a professional Ethical Hacker. He has been assigned the project of testing the
security of www.we-are-secure.com. He is using a tool to crack the wireless encryption keys. The
description of the tool is as follows:
Which of the following tools is John using to crack the wireless encryption keys?
Which of the following statements are true about volatile memory?
Which of the following statements are true about volatile memory? Each correct answer
represents a complete solution. Choose all that apply.
Which of the following logs will you review to accomplish the task?
You are a professional Computer Hacking forensic investigator. You have been called to collect
evidences of buffer overflow and cookie snooping attacks. Which of the following logs will you
review to accomplish the task? Each correct answer represents a complete solution. Choose all
that apply.
Which of the following scanning techniques will he use to accomplish this task?
John works as an Ethical Hacker for www.company.com Inc. He wants to find out the ports that
are open in www.company.com’s server using a port scanner. However, he does not want to
establish a full TCP connection. Which of the following scanning techniques will he use to
accomplish this task?
______________ is a prime example of a high-interaction honeypot
CORRECT TEXT
Fill in the blank with the appropriate term.
______________ is a prime example of a high-interaction honeypot.
Which of the following tools is an open source protocol analyzer that can capture traffic in real time?
Which of the following tools is an open source protocol analyzer that can capture traffic in real
time?
Which of the following tools are NOT used for logging network activities in the Linux operating system?
Which of the following tools are NOT used for logging network activities in the Linux operating
system? Each correct answer represents a complete solution. Choose all that apply.
The______________ model is a description framework for computer network protocols and is sometimes called the
CORRECT TEXT
Fill in the blank with the appropriate term.
The______________ model is a description framework for computer network protocols and is
sometimes called the Internet Model or the DoD Model.
What is the IP address of the sender of this email?
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic
project. Now, you want to know the IP address of the sender so that you can analyze various
information such as the actual location, domain information, operating system being used, contact
information, etc. of the email sender with the help of various tools and resources. You also want to
check whether this email is fake or real. You know that analysis of email headers is a good starting
point in such cases. The email header of the suspicious email is given below: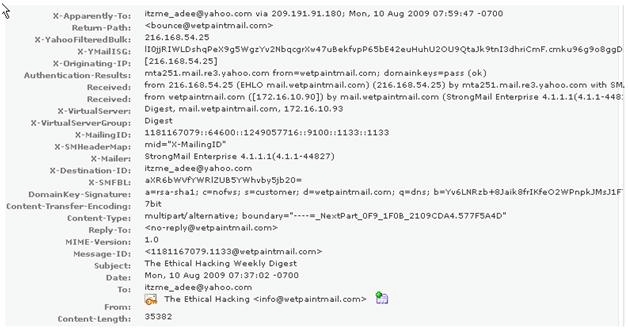
What is the IP address of the sender of this email?

