The role of the forensic investigator is to:
A forensic investigator is a person who handles the complete Investigation process, that is, the
preservation, identification, extraction, and documentation of the evidence. The investigator has
many roles and responsibilities relating to the cybercrime analysis. The role of the forensic
investigator is to:
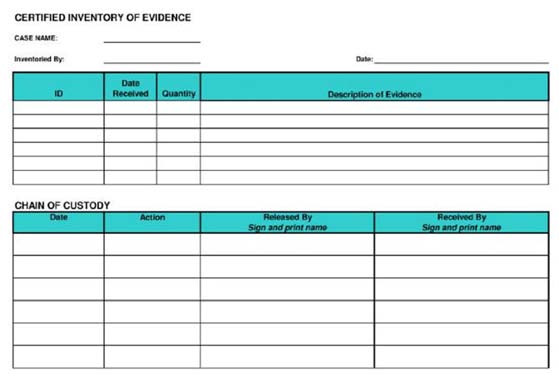
What document does the screenshot represent?
Which of the following standard is based on a legal precedent regarding the admissibility of scientific examin
Which of the following standard is based on a legal precedent regarding the admissibility of
scientific examinations or experiments in legal cases?
Temporal keys are changed for every____________.
Wi-Fi Protected Access (WPA) is a data encryption method for WLANs based on 802.11
standards. Temporal Key Integrity Protocol (TKIP) enhances WEP by adding a rekeying
mechanism to provide fresh encryption and integrity keys. Temporal keys are changed for
every____________.
Which of the following email clients he can use to analyze the DBX files?
Billy, a computer forensics expert, has recovered a large number of DBX files during forensic
investigation of a laptop. Which of the following email clients he can use to analyze the DBX files?
Which of the following is the certifying body of forensics labs that investigate criminal cases by analyzing e
Which of the following is the certifying body of forensics labs that investigate criminal cases by
analyzing evidence?
Raw data acquisition format creates ____________of a data set or suspect drive.
Raw data acquisition format creates ____________of a data set or suspect drive.
Which of the following attacks allows an attacker to access restricted directories…?
Which of the following attacks allows an attacker to access restricted directories, including
application source code, configuration and critical system files, and to execute commands outside
of the web server’s root directory?
The JPEG lossy algorithm divides the image in separate blocks of____________.
JPEG is a commonly used method of compressing photographic Images. It uses a compression
algorithm to minimize the size of the natural image, without affecting the quality of the image. The
JPEG lossy algorithm divides the image in separate blocks of____________.
Which of the following attacks allows attacker to acquire access to the communication channels between the vic
Which of the following attacks allows attacker to acquire access to the communication channels
between the victim and server to extract the information?