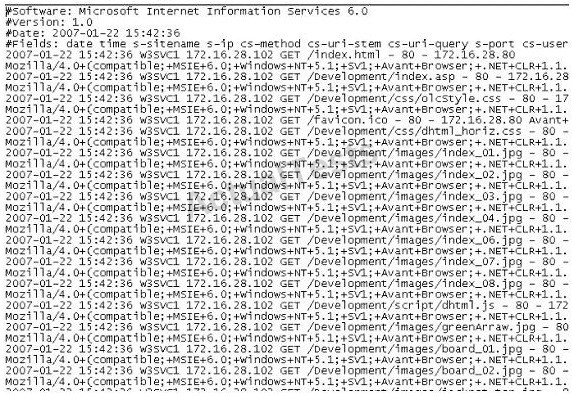
What time standard is used by IIS as seen in the screenshot?
which of the following statement holds true?
In the context of file deletion process, which of the following statement holds true?
What must an investigator do before disconnecting an iPod from any type of computer?
What must an investigator do before disconnecting an iPod from any type of computer?
What technique used by Encase makes it virtually impossible to tamper with evidence once it has been acquired?
What technique used by Encase makes it virtually impossible to tamper with evidence once it has been acquired?
What is one method of bypassing a system BIOS password?
What is one method of bypassing a system BIOS password?
what file system will be used?
When using an iPod and the host computer is running Windows, what file system will be used?
When carrying out a forensics investigation, why should you never delete a partition on a dynamic disk?
When carrying out a forensics investigation, why should you never delete a partition on a dynamic disk?
What type of file is represented by a colon (:) with a name following it in the Master File Table (MFT) of an
What type of file is represented by a colon (:) with a name following it in the Master File Table (MFT) of an NTFS disk?
What type of activity is the investigator seeing?
An investigator is searching through the firewall logs of a company and notices ICMP packets that are larger than 65,536 bytes.
What type of activity is the investigator seeing?
what legal term?
The efforts to obtain information before a trial by demanding documents, depositions, questions and answers written under oath, written requests for admissions of fact, and examination of the scene is a description of what legal term?