What is a chain of custody?
What is a chain of custody?
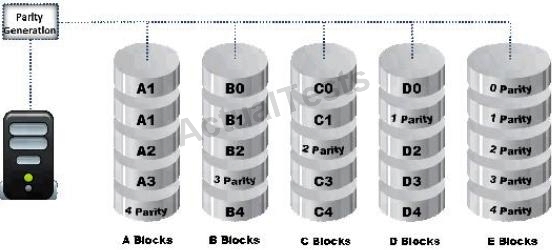
What RAID level is represented here?
Which of the following attributes of a forensics report can render it inadmissible in a court of law?
Computer forensics report provides detailed information on complete computer forensics
investigation process. It should explain how the incident occurred, provide technical details of the
incident and should be clear to understand. Which of the following attributes of a forensics report
can render it inadmissible in a court of law?
Email spoofing refers to:
Email spoofing refers to:
It helps to determine a logical timeline of the security incident and the users who would be responsible.
Volatile information can be easily modified or lost when the system is shut down or rebooted. It
helps to determine a logical timeline of the security incident and the users who would be
responsible.
A steganographic file system is a method to store the files in a way that encrypts and hides the data without
A steganographic file system is a method to store the files in a way that encrypts and hides the
data without the knowledge of others
which a packet should be forwarded toward its destination?
Which device in a wireless local area network (WLAN) determines the next network point to which
a packet should be forwarded toward its destination?
Data Acquisition is the process of imaging or otherwise obtaining information from a digital device and its pe
Data Acquisition is the process of imaging or otherwise obtaining information from a digital device
and its peripheral equipment and media
LBA (Logical Block Address) addresses data by allotting a ___________to each sector of the hard disk.
LBA (Logical Block Address) addresses data by allotting a ___________to each sector of the hard
disk.
Buffer overflow attacks allow an attacker to modify the _______________in order to control the process executi
Buffer Overflow occurs when an application writes more data to a block of memory, or buffer, than
the buffer is allocated to hold. Buffer overflow attacks allow an attacker to modify the
_______________in order to control the process execution, crash the process and modify internal
variables.