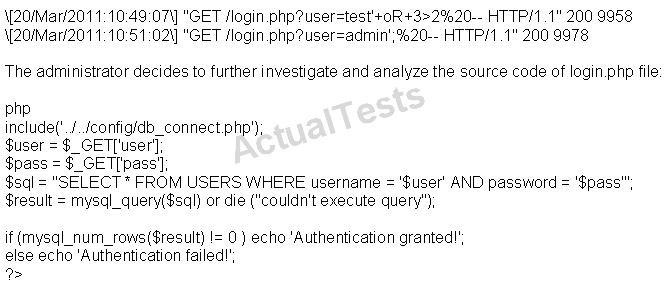
Based on source code analysis, the analyst concludes that the login.php script is vulnerable to…
What would be your inference?
Eric notices repeated probes to port 1080. He learns that the protocol being used is designed to
allow a host outside of a firewall to connect transparently and securely through the firewall. He
wonders if his firewall has been breached. What would be your inference?
Which is the most efficient technique should the tester consider using?
A penetration tester is attempting to scan an internal corporate network from the internet without
alerting the border sensor. Which is the most efficient technique should the tester consider using?
How can an attacker disguise his buffer overflow attack signature such that there is a greater probability of
Basically, there are two approaches to network intrusion detection: signature detection, and
anomaly detection. The signature detection approach utilizes well-known signatures for network
traffic to identify potentially malicious traffic. The anomaly detection approach utilizes a previous
history of network traffic to search for patterns that are abnormal, which would indicate an
intrusion. How can an attacker disguise his buffer overflow attack signature such that there is a
greater probability of his attack going undetected by the IDS?
which of the following layers of the OSI Model?
A circuit level gateway works at which of the following layers of the OSI Model?
which of the following options is he likely to choose?
John has a proxy server on his network which caches and filters web access. He shuts down all
unnecessary ports and services. Additionally, he has installed a firewall (Cisco PIX) that will not
allow users to connect to any outbound ports. Jack, a network user has successfully connected to
a remote server on port 80 using netcat. He could in turn drop a shell from the remote machine.
Assuming an attacker wants to penetrate John’s network, which of the following options is he likely
to choose?
Which of the following lists are valid data-gathering activities associated with a risk assessment?
Which of the following lists are valid data-gathering activities associated with a risk assessment?
A program that defends against a port scanner will attempt to:
A program that defends against a port scanner will attempt to:
Which of the following is the best remediation against this type of attack?
A network security administrator is worried about potential man-in-the-middle attacks when users
access a corporate web site from their workstations. Which of the following is the best remediation
against this type of attack?