Why is Jim having these problems?
Jim is having no luck performing a penetration test in XYZ’s network. He is running the tests from
home and has downloaded every security scanner that he could lay his hands on. Despite
knowing the IP range of all the systems, and the exact network configuration, Jim is unable to get
any useful results.
Why is Jim having these problems?
What could be the reason?
An attacker is attempting to telnet into a corporation’s system in the DMZ. The attacker doesn’t
want to get caught and is spoofing his IP address. After numerous tries he remains unsuccessful
in connecting to the system. The attacker rechecks that the target system is actually listening on
Port 23 and he verifies it with both nmap and hping2. He is still unable to connect to the target
system. What could be the reason?
What kind of assessment will you be performing ?
You have just received an assignment for an assessment at a company site. Company’s
management is concerned about external threat and wants to take appropriate steps to insure
security is in place. Anyway the management is also worried about possible threats coming from
inside the site, specifically from employees belonging to different Departments. What kind of
assessment will you be performing ?
what will be the response?
If an attacker’s computer sends an IPID of 31400 to a zombie (Idle Scanning) computer on an
open port, what will be the response?
What does black box testing mean?
What does black box testing mean?
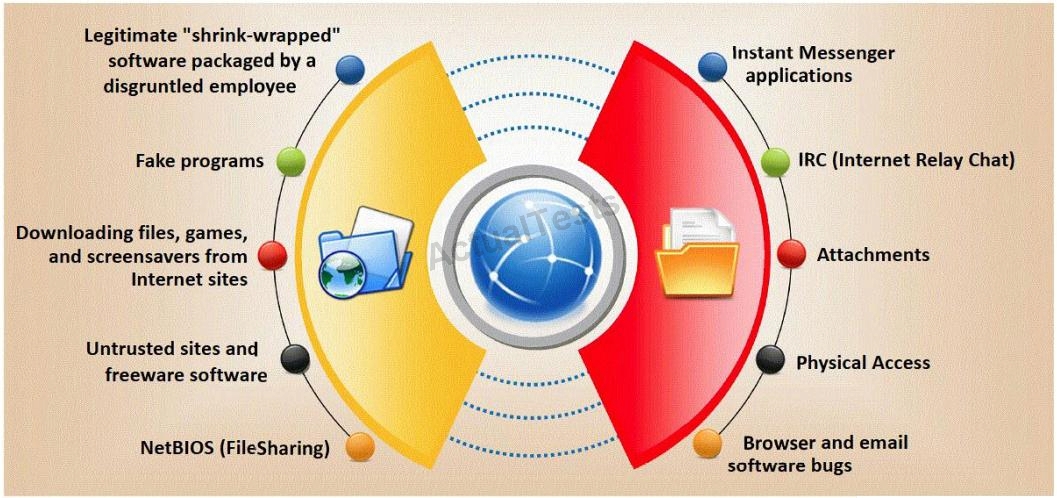
Which are the easiest and most convincing ways to infect a computer?
What do you think has occurred?
Bryan notices the error on the web page and asks Liza to enter liza’ or ‘1’=’1 in the email field.
They are greeted with a message “Your login information has been mailed to
johndoe@gmail.com”. What do you think has occurred?
Why do you think this could be a bad idea if there is an Intrusion Detection System deployed to monitor the tr
SSL has been seen as the solution to a lot of common security problems. Administrator will often
time make use of SSL to encrypt communications from points A to point B. Why do you think this
could be a bad idea if there is an Intrusion Detection System deployed to monitor the traffic
between point A and B?
What is wrong with the web application?
Liza has forgotten her password to an online bookstore. The web application asks her to key in her
email so that they can send her the password. Liza enters her email liza@yahoo.com’. The
application displays server error. What is wrong with the web application?
How can Jake gather network information in a secure manner?
Jake is a network administrator who needs to get reports from all the computer and network
devices on his network. Jake wants to use SNMP but is afraid that won’t be secure since
passwords and messages are in clear text. How can Jake gather network information in a secure
manner?