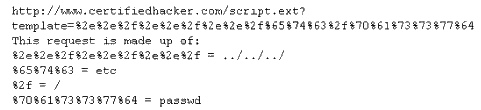
What address is that of the true originator of the message?
Mike Robertson PDF Reader Support Copyright Antivirus 2010 ?
You receive an e-mail like the one shown below. When you click on the link contained in the mail,
you are redirected to a website seeking you to download free Anti-Virus software.
Dear valued customers,
We are pleased to announce the newest version of Antivirus 2010 for Windows which will probe
you with total security against the latest spyware, malware, viruses, Trojans and other online
threats. Simply visit the link below and enter your antivirus code:
Antivirus code: 5014
http://www.juggyboy/virus/virus.html
Thank you for choosing us, the worldwide leader Antivirus solutions.
Mike Robertson
PDF Reader Support
Copyright Antivirus 2010 ?All rights reserved
If you want to stop receiving mail, please go to:
http://www.juggyboy.com
or you may contact us at the following address: Media Internet Consultants, Edif. Neptuno, Planta
Baja, Ave. Ricardo J. Alfaro, Tumba Muerto, n/a Panama
How will you determine if this is Real Anti-Virus or Fake Anti-Virus website?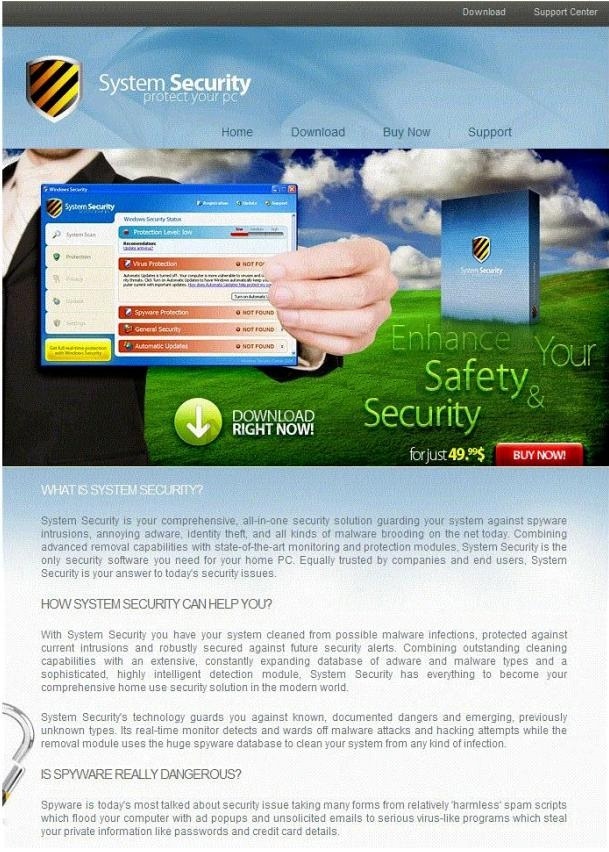
Which of the following lists the best options?
Bob wants to prevent attackers from sniffing his passwords on the wired network. Which of the
following lists the best options?
What is this document called?
Every company needs a formal written document which spells out to employees precisely what
they are allowed to use the company’s systems for, what is prohibited, and what will happen to
them if they break the rules. Two printed copies of the policy should be given to every employee
as soon as possible after they join the organization. The employee should be asked to sign one
copy, which should be safely filed by the company. No one should be allowed to use the
company’s computer systems until they have signed the policy in acceptance of its terms. What is
this document called?
Which tool/utility can help you extract the application layer data from each TCP connection from a log file in
Which tool/utility can help you extract the application layer data from each TCP connection from a
log file into separate files?
How would you protect from these attacks?
Which of the following display filters will you enable in Ethereal to view the three-way handshake for a conne
Which of the following display filters will you enable in Ethereal to view the three-way handshake
for a connection from host 192.168.0.1?
Which type of sniffing technique is generally referred as MiTM attack?
Which of the following tool accomplishes this?
When Jason moves a file via NFS over the company’s network, you want to grab a copy of it by
sniffing. Which of the following tool accomplishes this?
What happens when the CAM table becomes full?
Switches maintain a CAM Table that maps individual MAC addresses on the network to physical
ports on the switch.
In MAC flooding attack, a switch is fed with many Ethernet frames, each containing different
source MAC addresses, by the attacker. Switches have a limited memory for mapping various
MAC addresses to physical ports. What happens when the CAM table becomes full?