Identify the remote server’s port number by decoding the packet?
Jason’s Web server was attacked by a trojan virus. He runs protocol analyzer and notices that the
trojan communicates to a remote server on the Internet. Shown below is the standard “hexdump”
representation of the network packet, before being decoded. Jason wants to identify the trojan by
looking at the destination port number and mapping to a trojan-port number database on the
Internet. Identify the remote server’s port number by decoding the packet?
This TCP flag instructs the sending system to transmit all buffered data immediately.
This TCP flag instructs the sending system to transmit all buffered data immediately.
Which of the following Netcat commands would be used to perform a UDP scan of the lower 1024 ports?
Which of the following Netcat commands would be used to perform a UDP scan of the lower 1024
ports?
How would you proceed?
The network administrator at Spears Technology, Inc has configured the default gateway Cisco
router’s access-list as below: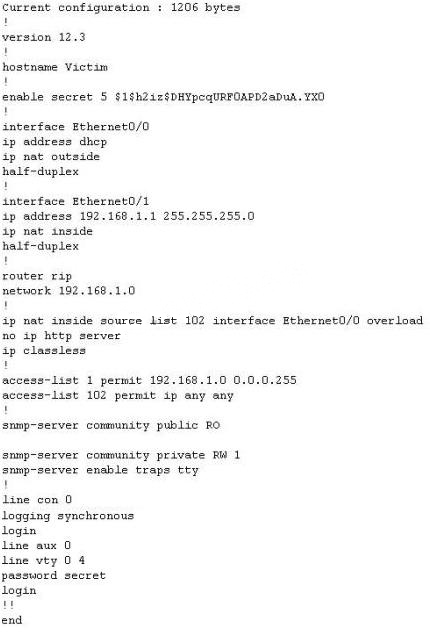
You are hired to conduct security testing on their network. You successfully brute-force the SNMP
community string using a SNMP crack tool. The access-list configured at the router prevents you
from establishing a successful connection. You want to retrieve the Cisco configuration from the
router. How would you proceed?
Sniffing is considered an active attack.
Sniffing is considered an active attack.
How will you achieve this without raising suspicion?
You work for Acme Corporation as Sales Manager. The company has tight network security
restrictions. You are trying to steal data from the company’s Sales database (Sales.xls) and
transfer them to your home computer. Your company filters and monitors traffic that leaves from
the internal network to the Internet. How will you achieve this without raising suspicion?
A file integrity program such as Tripwire protects against Trojan horse attacks by:
A file integrity program such as Tripwire protects against Trojan horse attacks by:
"mountd access";)
Study the snort rule given below and interpret the rule.
alert tcp any any –> 192.168.1.0/24 111 (content:”|00 01 86 a5|”; msG. “mountd access”;)
cell(?(c)????
Erik notices a big increase in UDP packets sent to port 1026 and 1027 occasionally. He enters the
following at the command prompt.
$ nc -l -p 1026 -u -v
In response, he sees the following message.
cell(?(c)????STOPALERT77STOP! WINDOWS REQUIRES IMMEDIATE ATTENTION.
Windows has found 47 Critical Errors.
To fix the errors please do the following:
1. Download Registry Repair from: www.reg-patch.com
2. Install Registry Repair
3. Run Registry Repair
4. Reboot your computer
FAILURE TO ACT NOW MAY LEAD TO DATA LOSS AND CORRUPTION!
What would you infer from this alert?
What port number is used by LDAP protocol?
What port number is used by LDAP protocol?

