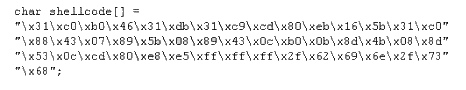what would be one of the last steps that would be taken to ensure that the compromise is not traced back to th
After an attacker has successfully compromised a remote computer, what would be one of the last
steps that would be taken to ensure that the compromise is not traced back to the source of the
problem?
What is Bob supposed to do next?
Bob is going to perform an active session hijack against Brownies Inc. He has found a target that
allows session oriented connections (Telnet) and performs the sequence prediction on the target
operating system. He manages to find an active session due to the high level of traffic on the
network. What is Bob supposed to do next?
Which command would you execute to extract the Trojan to a standalone file?
You have hidden a Trojan file virus.exe inside another file readme.txt using NTFS streaming.
Which command would you execute to extract the Trojan to a standalone file?
What is this technique called?
ViruXine.W32 virus hides their presence by changing the underlying executable code. This Virus
code mutates while keeping the original algorithm intact, the code changes itself each time it runs,
but the function of the code (its semantics) will not change at all.
Here is a section of the Virus code:
What is this technique called?
What is the next step you would do?
You suspect that your Windows machine has been compromised with a Trojan virus. When you
run anti-virus software it does not pick of the Trojan. Next you run netstat command to look for
open ports and you notice a strange port 6666 open.
What is the next step you would do?
"Testing the network using the same methodologies and tools employed by attackers" Identify the corr
“Testing the network using the same methodologies and tools employed by attackers” Identify the
correct terminology that defines the above statement.
In Linux, the three most common commands that hackers usually attempt to Trojan are:
In Linux, the three most common commands that hackers usually attempt to Trojan are:
what will be the result?
Nathan is testing some of his network devices. Nathan is using Macof to try and flood the ARP
cache of these switches. If these switches’ ARP cache is successfully flooded, what will be the
result?
What can he do to help ensure this?
John wishes to install a new application onto his Windows 2000 server.
He wants to ensure that any application he uses has not been Trojaned.
What can he do to help ensure this?