What is the name of this file?
Web servers often contain directories that do not need to be indexed. You create a text file with
search engine indexing restrictions and place it on the root directory of the Web Server.
User-agent: *
Disallow: /images/
Disallow: /banners/
Disallow: /Forms/
Disallow: /Dictionary/
Disallow: /_borders/
Disallow: /_fpclass/
Disallow: /_overlay/
Disallow: /_private/
Disallow: /_themes/
What is the name of this file?
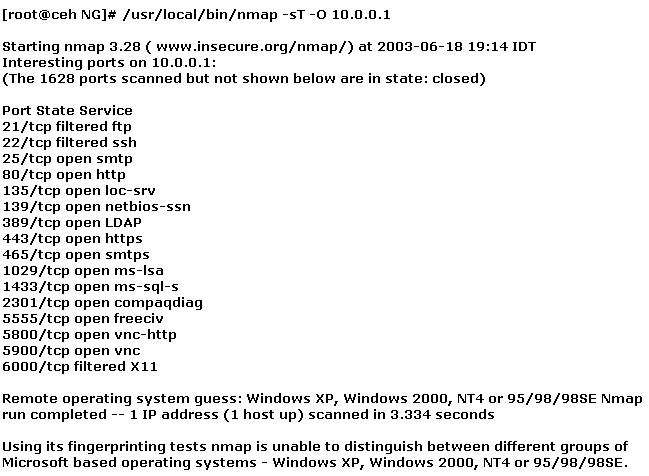
What operating system is the target host running based on the open ports shown above?
Which of the following comes as one of the last steps that should be taken to ensure that the compromise canno
An attacker has successfully compromised a remote computer. Which of the following comes as
one of the last steps that should be taken to ensure that the compromise cannot be traced back to
the source of the problem?
Why would an attacker want to perform a scan on port 137?
Why would an attacker want to perform a scan on port 137?
Study the log below and identify the scan type.
Which of the following commands extracts the HINFO record?
Attackers target HINFO record types stored on a DNS server to enumerate information. These are
information records and potential source for reconnaissance. A network administrator has the
option of entering host information specifically the CPU type and operating system when creating
a new DNS record. An attacker can extract this type of information easily from a DNS server.
Which of the following commands extracts the HINFO record?
Which Type of scan sends a packets with no flags set?
Which Type of scan sends a packets with no flags set? Select the Answer
What are some of the common vulnerabilities in web applications that he should be concerned about?
Bret is a web application administrator and has just read that there are a number of surprisingly
common web application vulnerabilities that can be exploited by unsophisticated attackers with
easily available tools on the Internet. He has also read that when an organization deploys a web
application, they invite the world to send HTTP requests. Attacks buried in these requests sail past
firewalls, filters, platform hardening, SSL, and IDS without notice because they are inside legal
HTTP requests. Bret is determined to weed out vulnerabilities.
What are some of the common vulnerabilities in web applications that he should be concerned
about?
What protocol is most likely to be listening on those ports?
Sandra has been actively scanning the client network on which she is doing a vulnerability
assessment test. While conducting a port scan she notices open ports in the range of 135 to 139.
What protocol is most likely to be listening on those ports?
What is War Dialing?
What is War Dialing?