What are the default passwords used by SNMP?
What are the default passwords used by SNMP? (Choose two.)
What port number is used by Kerberos protocol?
What port number is used by Kerberos protocol?
Which of the following ICMP message types are used for destinations unreachables?
Which of the following ICMP message types are used for destinations unreachables?
What does FIN in TCP flag define?
What does FIN in TCP flag define?
What is the proper response for a FIN scan if the port is closed?
What is the proper response for a FIN scan if the port is closed?
Why do you think this is possible?
Annie has just succeeded in stealing a secure cookie via a XSS attack. She is able to replay the
cookie even while the session is invalid on the server. Why do you think this is possible?
What is the proper response for a X-MAS scan if the port is closed?
What is the proper response for a X-MAS scan if the port is closed?
This attack technique is used when a Web application is vulnerable to an SQL Injection but the results of the
This attack technique is used when a Web application is vulnerable to an SQL Injection but the
results of the Injection are not visible to the attacker.
What flags are set in a X-MAS scan?
What flags are set in a X-MAS scan?(Choose all that apply.
How do you ensure if the e-mail is authentic and sent from fedex.com?
A common technique for luring e-mail users into opening virus-launching attachments is to send
messages that would appear to be relevant or important to many of their potential recipients. One
way of accomplishing this feat is to make the virus-carrying messages appear to come from some
type of business entity retailing sites, UPS, FEDEX, CITIBANK or a major provider of a common
service.
Here is a fraudulent e-mail claiming to be from FedEx regarding a package that could not be
delivered. This mail asks the receiver to open an attachment in order to obtain the FEDEX tracking
number for picking up the package. The attachment contained in this type of e-mail activates a
virus.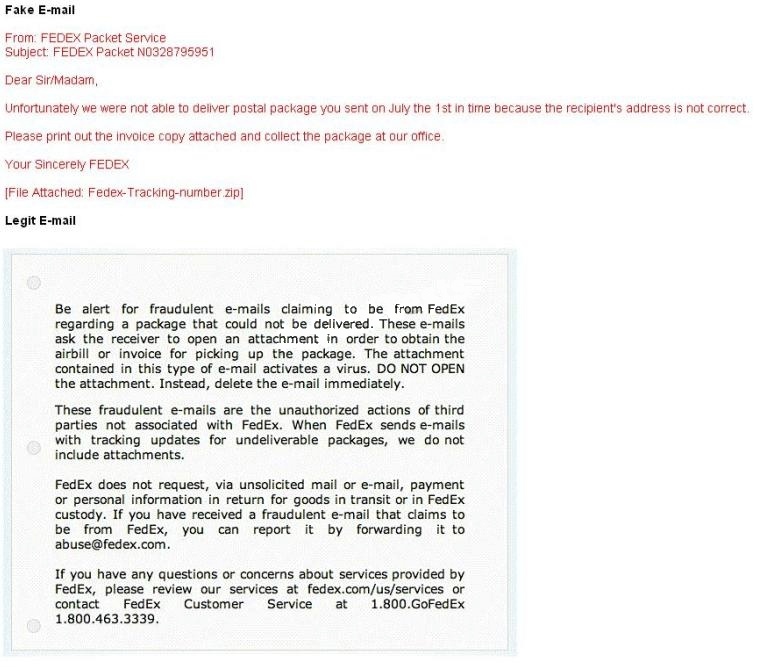
Vendors send e-mails like this to their customers advising them not to open any files attached with
the mail, as they do not include attachments.
Fraudulent e-mail and legit e-mail that arrives in your inbox contain the fedex.com as the sender of
the mail.
How do you ensure if the e-mail is authentic and sent from fedex.com?

