What port scanning method involves sending spoofed packets to a target system and then looking for adjustments
What port scanning method involves sending spoofed packets to a target system and then looking
for adjustments to the IPID on a zombie system?
What is the correct command to run Netcat on a server using port 56 that spawns command shell when connected?
What port scanning method is the most reliable but also the most detectable?
What port scanning method is the most reliable but also the most detectable?
SNMP is a connectionless protocol that uses UDP instead of TCP packets (True or False)
SNMP is a connectionless protocol that uses UDP instead of TCP packets (True or False)
What does an ICMP (Code 13) message normally indicates?
What does an ICMP (Code 13) message normally indicates?
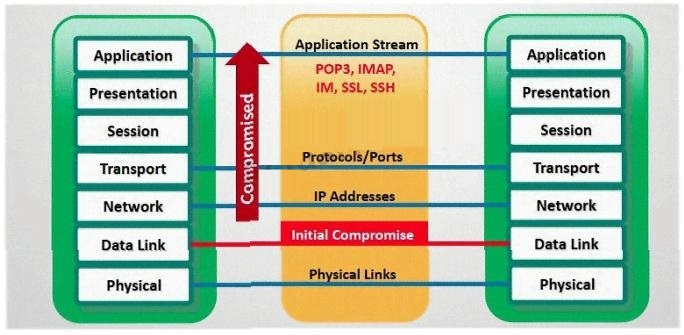
which OSI layer?
TCP/IP Session Hijacking is carried out in which OSI layer?
Because UDP is a connectionless protocol: (Select 2)
Because UDP is a connectionless protocol: (Select 2)
which part of OSI layer, ARP Poisoning occurs?
What ICMP message types are used by the ping command?
What ICMP message types are used by the ping command?
How will you accomplish this?
You want to hide a secret.txt document inside c:\windows\system32\tcpip.dll kernel library using
ADS streams. How will you accomplish this?