Which kind of scan would you use to achieve this?
You are scanning into the target network for the first time. You find very few conventional ports
open. When you attempt to perform traditional service identification by connecting to the open
ports, it yields either unreliable or no results. You are unsure of which protocols are being used.
You need to discover as many different protocols as possible.
Which kind of scan would you use to achieve this? (Choose the best answer)
How many bits encryption does SHA-1 use?
How many bits encryption does SHA-1 use?
What are two types of ICMP code used when using the ping command?
What are two types of ICMP code used when using the ping command?
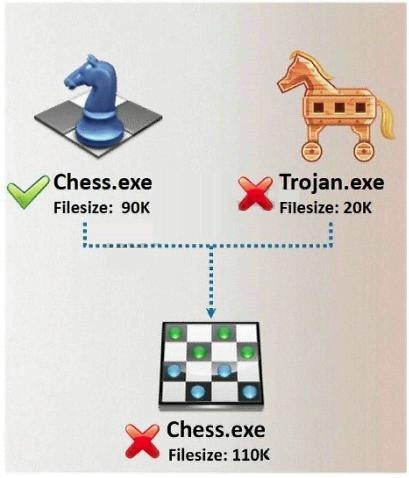
what is required to create the executable file chess.exe as shown below?
Which one of the following statements is probably true?
You are having problems while retrieving results after performing port scanning during internal
testing. You verify that there are no security devices between you and the target system. When
both stealth and connect scanning do not work, you decide to perform a NULL scan with NMAP.
The first few systems scanned shows all ports open.
Which one of the following statements is probably true?
What default port Syslog daemon listens on?
Syslog is a standard for logging program messages. It allows separation of the software that
generates messages from the system that stores them and the software that reports and analyzes
them. It also provides devices, which would otherwise be unable to communicate a means to
notify administrators of problems or performance.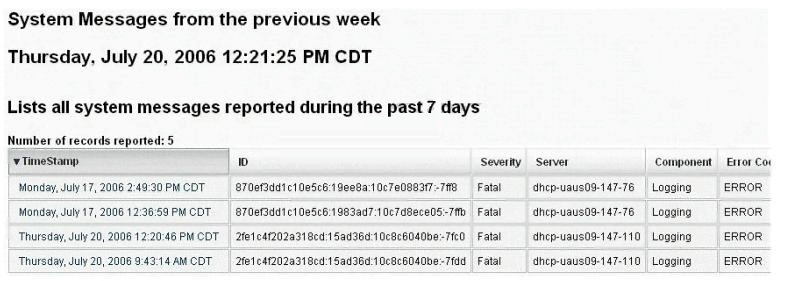
What default port Syslog daemon listens on?
What would you suggest to John to help identify the OS that is being used on the remote web server?
John has scanned the web server with NMAP. However, he could not gather enough information
to help him identify the operating system running on the remote host accurately.
What would you suggest to John to help identify the OS that is being used on the remote web
server?
Attackers send a legitimate-looking e-mail asking users to update their information on the company’s Web
This attack uses social engineering techniques to trick users into accessing a fake Web site and
divulging personal information. Attackers send a legitimate-looking e-mail asking users to update
their information on the company’s Web site, but the URLs in the e-mail actually point to a false
Web site.
What does this suggest?
An Nmap scan shows the following open ports, and nmap also reports that the OS guessing
results to match too many signatures hence it cannot reliably be identified:
21 ftp
23 telnet
80 http
443 https
What does this suggest?
Which of the following statements would NOT be a proper definition for a Trojan Horse?
Which of the following statements would NOT be a proper definition for a Trojan Horse?