Which of these would be a cause for alarm?
Network Administrator Patricia is doing an audit of the network. Below are some of her findings
concerning DNS. Which of these would be a cause for alarm?
Select the best answer.
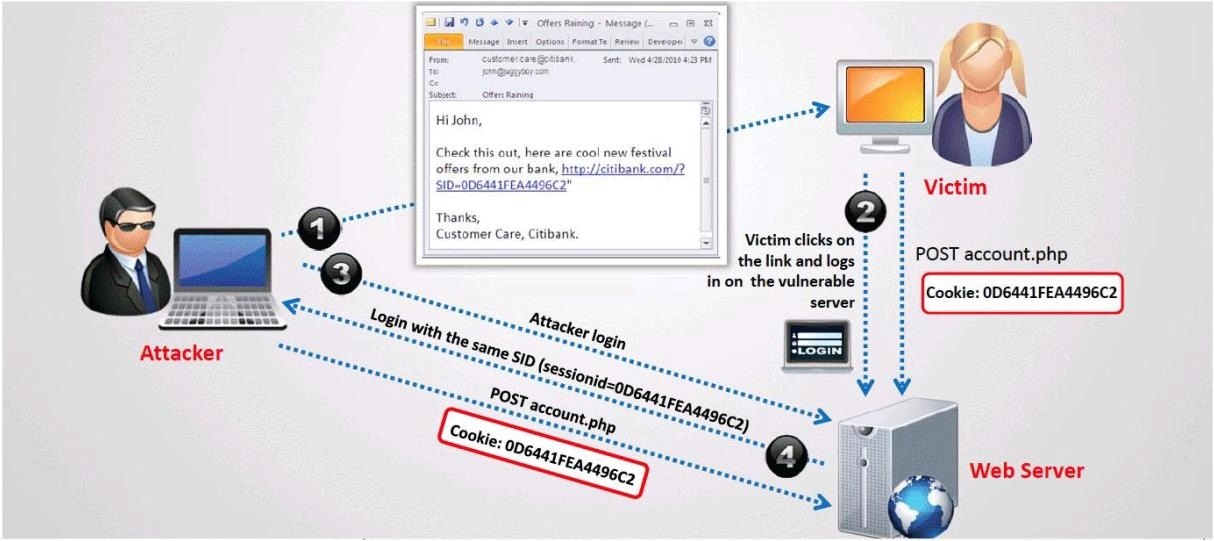
What type of session hijacking attack is shown in the exhibit?
What does the first and second column mean?
How do you protect your network against SYN Flood attacks?
The SYN flood attack sends TCP connections requests faster than a machine can process them.
Attacker creates a random source address for each packet
SYN flag set in each packet is a request to open a new connection to the server from the
spoofed IP address
Victim responds to spoofed IP address,then waits for confirmation that never arrives (timeout
wait is about 3 minutes)
Victim’s connection table fills up waiting for replies and ignores new connections
Legitimate users are ignored and will not be able to access the server
How do you protect your network against SYN Flood attacks?
What is the most likely cause behind this response?
While performing a ping sweep of a subnet you receive an ICMP reply of Code 3/Type 13 for all
the pings sent out.
What is the most likely cause behind this response?
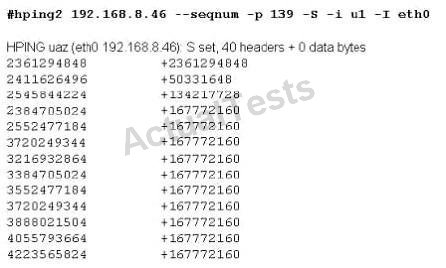
What type of port scan is shown below?
What can you infer from the above log?
The following excerpt is taken from a honeyput log. The log captures activities across three days.
There are several intrusion attempts; however, a few are successful. Study the log given below
and answer the following question:
(Note: The objective of this questions is to test whether the student has learnt about passive OS
fingerprinting (which should tell them the OS from log captures): can they tell a SQL injection
attack signature; can they infer if a user ID has been created by an attacker and whether they can
read plain source – destination entries from log entries.)
What can you infer from the above log?
What should Stephanie use so that she does not get in trouble for surfing the Internet?
Stephanie works as a records clerk in a large office building in downtown Chicago. On Monday,
she went to a mandatory security awareness class (Security5) put on by her company’s IT
department. During the class, the IT department informed all employees that everyone’s Internet
activity was thenceforth going to be monitored.
Stephanie is worried that her Internet activity might give her supervisor reason to write her up, or
worse get her fired. Stephanie’s daily work duties only consume about four hours of her time, so
she usually spends the rest of the day surfing the web. Stephanie really enjoys surfing the Internet
but definitely does not want to get fired for it.
What should Stephanie use so that she does not get in trouble for surfing the Internet?
what phase is Bob involved with?
Bob has been hired to perform a penetration test on XYZ.com. He begins by looking at IP address
ranges owned by the company and details of domain name registration. He then goes to News
Groups and financial web sites to see if they are leaking any sensitive information of have any
technical details online.
Within the context of penetration testing methodology, what phase is Bob involved with?
What type of port will Neil need to setup in order to accomplish this?
Neil is a network administrator working in Istanbul. Neil wants to setup a protocol analyzer on his
network that will receive a copy of every packet that passes through the main office switch. What
type of port will Neil need to setup in order to accomplish this?