what concept in the realm of email security?
To what does “message repudiation” refer to what concept in the realm of email security?
How will you delete the OrdersTable from the database using SQL Injection?
The following script shows a simple SQL injection. The script builds an SQL query by
concatenating hard-coded strings together with a string entered by the user: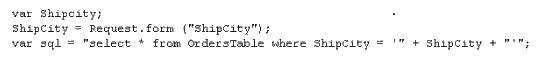
The user is prompted to enter the name of a city on a Web form. If she enters Chicago, the query
assembled by the script looks similar to the following:
SELECT * FROM OrdersTable WHERE ShipCity = ‘Chicago’
How will you delete the OrdersTable from the database using SQL Injection?
What is odd about this attack?
Snort has been used to capture packets on the network. On studying the packets, the penetration
tester finds it to be abnormal. If you were the penetration tester, why would you find this
abnormal?
What is odd about this attack? (Choose the most appropriate statement)
What are the limitations of Vulnerability scanners?
What are the limitations of Vulnerability scanners? (Select 2 answers)
which are the four existing Regional Internet Registry (RIR’s)?
Your XYZ trainee Sandra asks you which are the four existing Regional Internet Registry (RIR’s)?
Where can Stephanie go to see past versions and pages of a website?
Stephanie works as senior security analyst for a manufacturing company in Detroit. Stephanie
manages network security throughout the organization. Her colleague Jason told her in confidence
that he was able to see confidential corporate information posted on the external website
http://www.jeansclothesman.com. He tries random URLs on the company’s website and finds
confidential information leaked over the web. Jason says this happened about a month ago.
Stephanie visits the said URLs, but she finds nothing. She is very concerned about this, since
someone should be held accountable if there was sensitive information posted on the website.
Where can Stephanie go to see past versions and pages of a website?
A very useful resource for passively gathering information about a target company is:
A very useful resource for passively gathering information about a target company is:
Why do you think Dan might not be able to get an interactive session?
Dan is conducting penetration testing and has found a vulnerability in a Web Application which
gave him the sessionID token via a cross site scripting vulnerability. Dan wants to replay this
token. However, the session ID manager (on the server) checks the originating IP address as well.
Dan decides to spoof his IP address in order to replay the sessionID. Why do you think Dan might
not be able to get an interactive session?
What is the obstructed IP address in the e-mail URL?
You receive an email with the following message:
Hello Steve,
We are having technical difficulty in restoring user database record after the recent blackout. Your
account data is corrupted. Please logon to the SuperEmailServices.com and change your
password.
http://www.supermailservices.com@0xde.0xad.0xbe.0xef/support/logon.htm
If you do not reset your password within 7 days, your account will be permanently disabled locking
you out from our e-mail services.
Sincerely,
Technical Support
SuperEmailServices
From this e-mail you suspect that this message was sent by some hacker since you have been
using their e-mail services for the last 2 years and they have never sent out an e-mail such as this.
You also observe the URL in the message and confirm your suspicion about
0xde.0xad.0xbde.0xef which looks like hexadecimal numbers. You immediately enter the following
at Windows 2000 command prompt:
Ping 0xde.0xad.0xbe.0xef
You get a response with a valid IP address.
What is the obstructed IP address in the e-mail URL?
What technique has Jason most likely used?
Jason works in the sales and marketing department for a very large advertising agency located in
Atlanta. Jason is working on a very important marketing campaign for his company’s largest client.
Before the project could be completed and implemented, a competing advertising company comes
out with the exact same marketing materials and advertising, thus rendering all the work done for
Jason’s client unusable. Jason is questioned about this and says he has no idea how all the
material ended up in the hands of a competitor.
Without any proof, Jason’s company cannot do anything except move on. After working on
another high profile client for about a month, all the marketing and sales material again ends up in
the hands of another competitor and is released to the public before Jason’s company can finish
the project. Once again, Jason says that he had nothing to do with it and does not know how this
could have happened. Jason is given leave with pay until they can figure out what is going on.
Jason’s supervisor decides to go through his email and finds a number of emails that were sent to
the competitors that ended up with the marketing material. The only items in the emails were
attached jpg files, but nothing else. Jason’s supervisor opens the picture files, but cannot find
anything out of the ordinary with them.
What technique has Jason most likely used?

