What can Wayne infer from this traffic log?
Wayne is the senior security analyst for his company. Wayne is examining some traffic logs on a
server and came across some inconsistencies. Wayne finds some IP packets from a computer
purporting to be on the internal network. The packets originate from 192.168.12.35 with a TTL of
15. The server replied to this computer and received a response from 192.168.12.35 with a TTL of
21. What can Wayne infer from this traffic log?
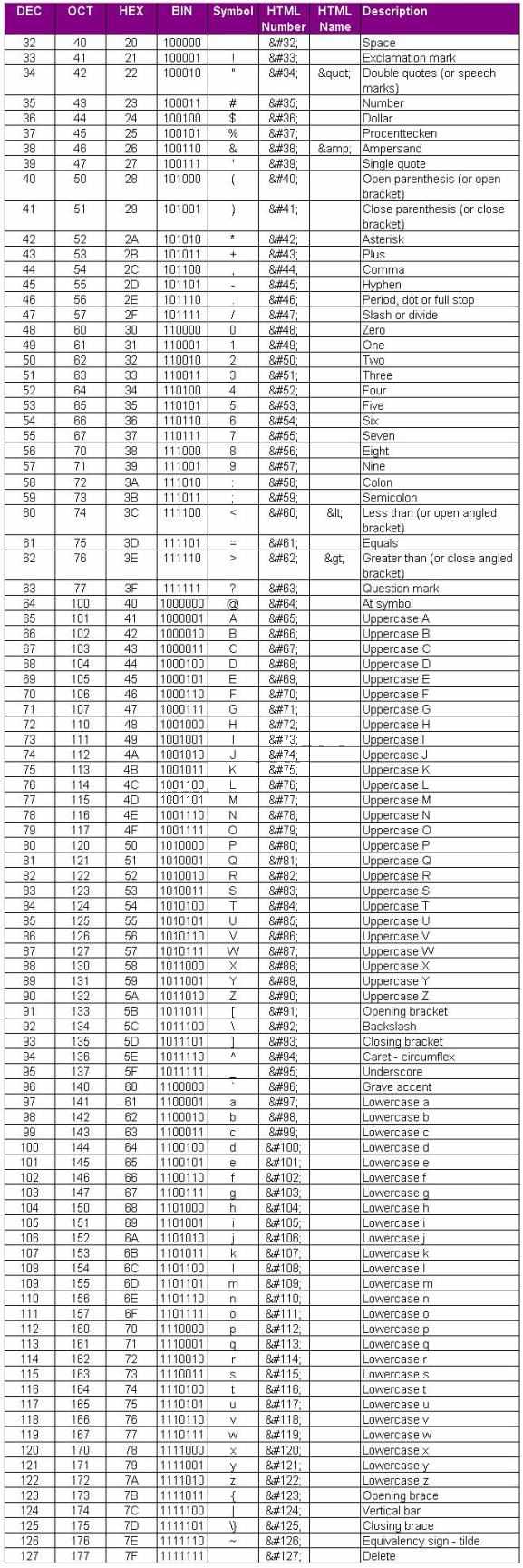
What type of port scan is shown below?
What is the correct syntax?
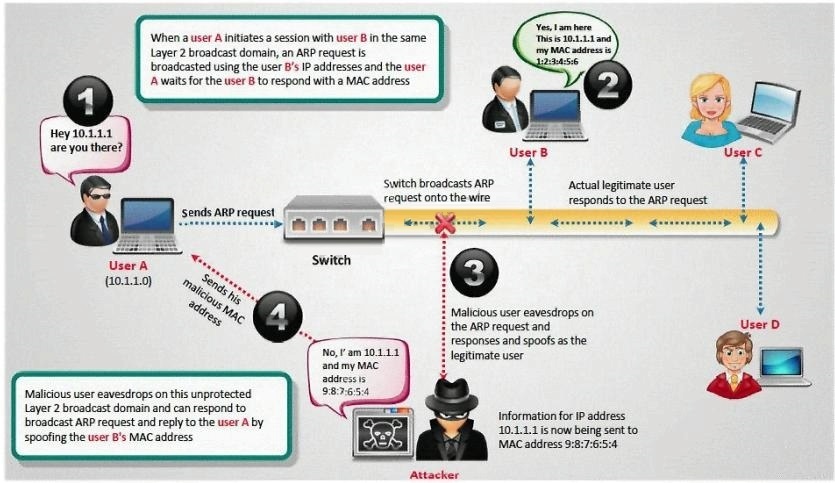
How do you defend against ARP Poisoning attack?
How can you achieve this?
You are the security administrator for a large network. You want to prevent attackers from running
any sort of traceroute into your DMZ and discovering the internal structure of publicly accessible
areas of the network. How can you achieve this?
What type of social engineering attack has Neil employed here?
Neil is an IT security consultant working on contract for Davidson Avionics. Neil has been hired to
audit the network of Davidson Avionics. He has been given permission to perform any tests
necessary. Neil has created a fake company ID badge and uniform. Neil waits by one of the
company’s entrance doors and follows an employee into the office after they use their valid access
card to gain entrance. What type of social engineering attack has Neil employed here?
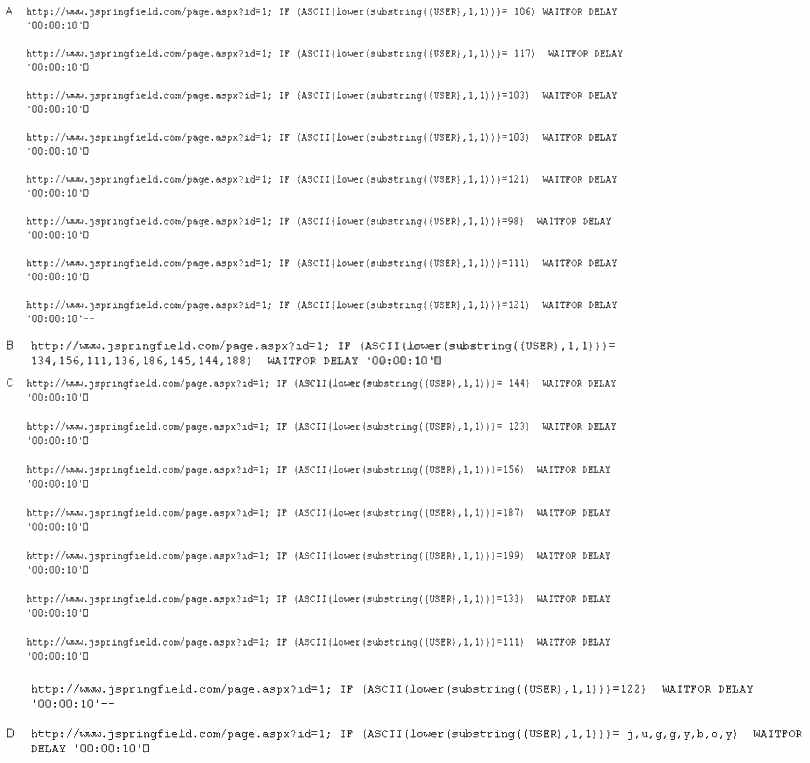
What attacks can you successfully launch against a server using the above technique?
After a client sends a connection request (SYN) packet to the server, the server will respond
(SYN-ACK) with a sequence number of its choosing, which then must be acknowledged (ACK) by
the client. This sequence number is predictable; the attack connects to a service first with its own
IP address, records the sequence number chosen, and then opens a second connection from a
forged IP address. The attack doesn’t see the SYN-ACK (or any other packet) from the server, but
can guess the correct responses. If the source IP address is used for authentication, then the
attacker can use the one-sided communication to break into the server. What attacks can you
successfully launch against a server using the above technique?
Which of the following represent weak password?
Which of the following represent weak password? (Select 2 answers)
What kind of software could Harold use to accomplish this?
Harold just got home from working at Henderson LLC where he works as an IT technician. He was
able to get off early because they were not too busy. When he walks into his home office, he
notices his teenage daughter on the computer, apparently chatting with someone online. As soon
as she hears Harold enter the room, she closes all her windows and tries to act like she was
playing a game. When Harold asks her what she was doing, she acts very nervous and does not
give him a straight answer. Harold is very concerned because he does not want his daughter to
fall victim to online predators and the sort. Harold doesn’t necessarily want to install any programs
that will restrict the sites his daughter goes to, because he doesn’t want to alert her to his trying to
figure out what she is doing. Harold wants to use some kind of program that will track her activities
online, and send Harold an email of her activity once a day so he can see what she has been up
to. What kind of software could Harold use to accomplish this?
what type of scan should you run to get very reliable results?
You are performing a port scan with nmap. You are in hurry and conducting the scans at the
fastest possible speed. However, you don’t want to sacrifice reliability for speed. If stealth is not an
issue, what type of scan should you run to get very reliable results?