How can Bill accomplish this?
Bill is a security analyst for his company. All the switches used in the company’s office are Cisco
switches. Bill wants to make sure all switches are safe from ARP poisoning. How can Bill
accomplish this?
What is the length of the MD5 hash?
Which type of password cracking technique works like dictionary attack but adds some numbers and symbols to th
Which type of password cracking technique works like dictionary attack but adds some numbers
and symbols to the words from the dictionary and tries to crack the password?
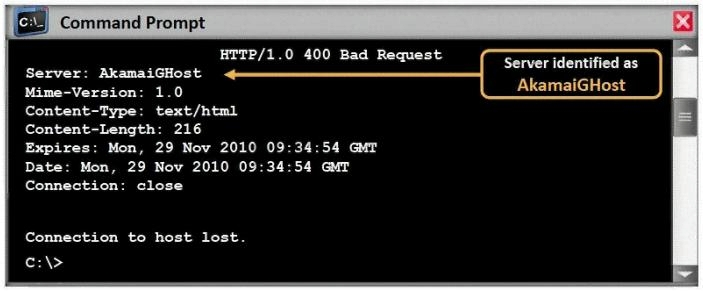
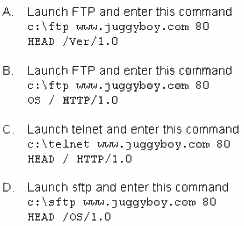
What command would you type to OS fingerprint a server using the command line?
What do you call a pre-computed hash?
What do you call a pre-computed hash?
Why attackers use proxy servers?
Why attackers use proxy servers?
How would you keep intruders from getting sensitive information regarding the network devices using SNMP?
The SNMP Read-Only Community String is like a password. The string is sent along with each
SNMP Get-Request and allows (or denies) access to a device. Most network vendors ship their
equipment with a default password of “public”. This is the so-called “default public community
string”. How would you keep intruders from getting sensitive information regarding the network
devices using SNMP? (Select 2 answers)
Which of the following countermeasures will NOT be effective against this attack?
You are writing security policy that hardens and prevents Footprinting attempt by Hackers. Which
of the following countermeasures will NOT be effective against this attack?
What kind of attack did the Hacker attempt to carry out at the bank?
Bank of Timbuktu is a medium-sized, regional financial institution in Timbuktu. The bank has
deployed a new Internet-accessible Web application recently. Customers can access their account
balances, transfer money between accounts, pay bills and conduct online financial business using
a Web browser.
John Stevens is in charge of information security at Bank of Timbuktu. After one month in
production, several customers have complained about the Internet enabled banking application.
Strangely, the account balances of many of the bank’s customers had been changed! However,
money hasn’t been removed from the bank; instead, money was transferred between accounts.
Given this attack profile, John Stevens reviewed the Web application’s logs and found the
following entries:
What kind of attack did the Hacker attempt to carry out at the bank?
How will you stop web spiders from crawling certain directories on your website?
WWW wanderers or spiders are programs that traverse many pages in the World Wide Web by
recursively retrieving linked pages. Search engines like Google, frequently spider web pages for
indexing. How will you stop web spiders from crawling certain directories on your website?