What is Jason trying to accomplish here?
In TCP communications there are 8 flags; FIN, SYN, RST, PSH, ACK, URG, ECE, CWR. These
flags have decimal numbers assigned to them:
FIN = 1
SYN = 2
RST = 4
PSH = 8
ACK = 16
URG = 32
ECE = 64
CWR = 128
Jason is the security administrator of ASPEN Communications. He analyzes some traffic using
Wireshark and has enabled the following filters.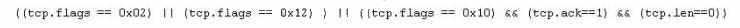
What is Jason trying to accomplish here?
How can she accomplish this?
Jayden is a network administrator for her company. Jayden wants to prevent MAC spoofing on all
the Cisco switches in the network. How can she accomplish this?
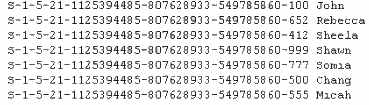
Here is the output of the SIDs: From the above list identify the user account with System Administrator priv
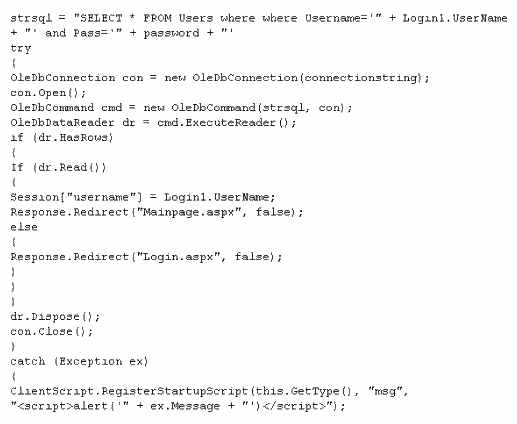
What is the problem with this ASP script (login.asp)?
How would you prevent Google from storing your search keywords?
Google uses a unique cookie for each browser used by an individual user on a computer. This
cookie contains information that allows Google to identify records about that user on its database.
This cookie is submitted every time a user launches a Google search, visits a site using AdSense
etc. The information stored in Google’s database, identified by the cookie, includes
Everything you search for using Google
Every web page you visit that has Google Adsense ads
How would you prevent Google from storing your search keywords?
How many bits encryption does SHA-1 use?
How many bits encryption does SHA-1 use?
what is required to create the executable file chess.exe as shown below?
What default port Syslog daemon listens on?
Syslog is a standard for logging program messages. It allows separation of the software that
generates messages from the system that stores them and the software that reports and analyzes
them. It also provides devices, which would otherwise be unable to communicate a means to
notify administrators of problems or performance.
What default port Syslog daemon listens on?
Attackers send a legitimate-looking e-mail asking users to update their information on the company’s Web
This attack uses social engineering techniques to trick users into accessing a fake Web site and
divulging personal information. Attackers send a legitimate-looking e-mail asking users to update
their information on the company’s Web site, but the URLs in the e-mail actually point to a false
Web site.
Which of the following statements would NOT be a proper definition for a Trojan Horse?
Which of the following statements would NOT be a proper definition for a Trojan Horse?