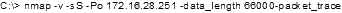Why are Linux/Unix based computers better to use than Windows computers for idle scanning?
Why are Linux/Unix based computers better to use than Windows computers for idle scanning?
How many bits is Source Port Number in TCP Header packet?
How many bits is Source Port Number in TCP Header packet?
Why are Linux/Unix based computers better to use than Windows computers for idle scanning?
Why are Linux/Unix based computers better to use than Windows computers for idle scanning?
What is Simon trying to accomplish here?
Simon is a former employee of Trinitron XML Inc. He feels he was wrongly terminated and wants
to hack into his former company’s network. Since Simon remembers some of the server names,
he attempts to run the axfr and ixfr commands using DIG. What is Simon trying to accomplish
here?
What is the result of this test?
You are carrying out the last round of testing for your new website before it goes live. The website
has many dynamic pages and connects to a SQL backend that accesses your product inventory in
a database. You come across a web security site that recommends inputting the following code
into a search field on web pages to check for vulnerabilities:
<script>alert(“This is a test.”)</script>
When you type this and click on search, you receive a pop-up window that says:
“This is a test.”
What is the result of this test?
Why is that?
After attending a CEH security seminar, you make a list of changes you would like to perform on
your network to increase its security. One of the first things you change is to switch the
RestrictAnonymous setting from 0 to 1 on your servers. This, as you were told, would prevent
anonymous users from establishing a null session on the server. Using Userinfo tool mentioned at
the seminar, you succeed in establishing a null session with one of the servers. Why is that?
What will the following command accomplish?
What are the security risks of running a "repair" installation for Windows XP?
What are the security risks of running a “repair” installation for Windows XP?
What tool could you use to get this information?
You are the security analyst working for a private company out of France. Your current assignment
is to obtain credit card information from a Swiss bank owned by that company. After initial
reconnaissance, you discover that the bank security defenses are very strong and would take too
long to penetrate. You decide to get the information by monitoring the traffic between the bank and
one of its subsidiaries in London. After monitoring some of the traffic, you see a lot of FTP packets
traveling back and forth. You want to sniff the traffic and extract usernames and passwords. What
tool could you use to get this information?
What filter should George use in Ethereal?
George is the network administrator of a large Internet company on the west coast. Per corporate
policy, none of the employees in the company are allowed to use FTP or SFTP programs without
obtaining approval from the IT department. Few managers are using SFTP program on their
computers. Before talking to his boss, George wants to have some proof of their activity.
George wants to use Ethereal to monitor network traffic, but only SFTP traffic to and from his
network. What filter should George use in Ethereal?