Which of the following fuzz testing she will perform where she can supply specific data to the application to
Fuzz testing or fuzzing is a software/application testing technique used to discover coding
errors and security loopholes in software, operating systems, or networks by inputting
massive amounts of random data, called fuzz, to the system in an attempt to make it crash.
Fuzzers work best for problems that can cause a program to crash, such as buffer overflow,
cross-site scripting, denial of service attacks, format bugs, and SQL injection. Fuzzer helps
to generate and submit a large number of inputs supplied to the application for testing it
against the inputs. This will help us to identify the SQL inputs that generate malicious output.
Suppose a pen tester knows the underlying structure of the database used by the application
(i.e., name, number of columns, etc.) that she is testing. Which of the following fuzz testing
she will perform where she can supply specific data to the application to discover
vulnerabilities?
which one of the following?
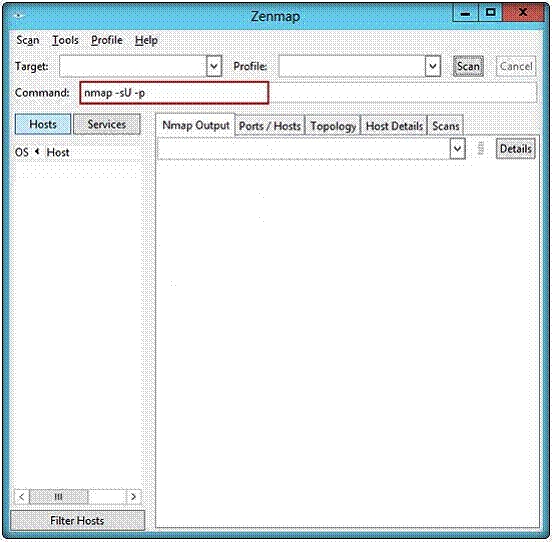
Which one of the following Nmap commands will he use to find it?
what does blue teaming mean?
Identify the port numbers used by POP3 and POP3S protocols.
Identify the port numbers used by POP3 and POP3S protocols.
Which of the following can the attacker use to launch an SQL injection attack?
SQL injection attacks are becoming significantly more popular amongst hackers and there
has been an estimated 69 percent increase of this attack type. This exploit is used to great
effect by the hacking community since it is the primary way to steal sensitive data from web
applications. It takes advantage of non-validated input vulnerabilities to pass SQL
commands through a web application for execution by a backend database. The below
diagram shows how attackers launchedSQL injection attacks on web applications.
Which of the following can the attacker use to launch an SQL injection attack?
Which of the following methods of attempting social engineering is associated with bribing, handing out gifts&
The objective of social engineering pen testing is to test the strength of human factors in a
security chain within the organization. It is often used to raise the level of security awareness
among employees.
The tester should demonstrate extreme care and professionalism during a social
engineering pen test as it might involve legal issues such as violation of privacy and may
result in an embarrassing situation for the organization. Which of the following methods of
attempting social engineering is associated with bribing, handing out gifts, and becoming
involved in a personal relationship to befriend someone inside the company?
What threat categories should you use to prioritize vulnerabilities detected in the pen testing report?
What threat categories should you use to prioritize vulnerabilities detected in the pen testing
report?
Which of the following has an offset field that specifies the length of the header and data?
Which of the following has an offset field that specifies the length of the header and data?
What is the formula to calculate risk?
Many security and compliance projects begin with a simple idea: assess the organization’s
risk, vulnerabilities, and breaches. Implementing an IT security risk assessment is critical to
the overall security posture of any organization. An effective security risk assessment can
prevent breaches and reduce the impact of realized breaches.
What is the formula to calculate risk?