Which of the following attributes has a LM and NTLMv1 value as 64bit + 64bit + 64bit and NTLMv2 value as 128 b
Which of the following attributes has a LM and NTLMv1 value as 64bit + 64bit + 64bit and
NTLMv2 value as 128 bits?
Which of the following password hashing algorithms is used in the NTLMv2 authentication mechanism?
Which of the following password hashing algorithms is used in the NTLMv2 authentication
mechanism?
Identify the attack represented in the diagram below:
Which of the following is developed to address security concerns on time and reduce the misuse or threat of at
Which of the following is developed to address security concerns on time and reduce the
misuse or threat of attacks in an organization?
Which of the following equipment could a pen tester use to perform shoulder surfing?
Which of the following equipment could a pen tester use to perform shoulder surfing?
What is the criminal practice of social engineering where an attacker uses the telephone system in an attempt
The term social engineering is used to describe the various tricks used to fool people
(employees, business partners, or customers) into voluntarily giving away information that
would not normally be known to the general public.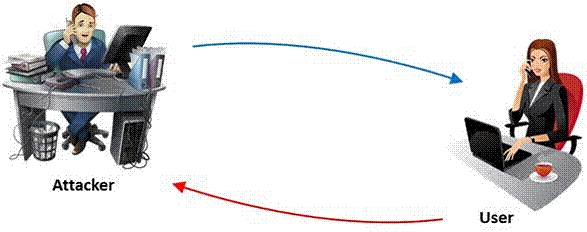
What is the criminal practice of social engineering where an attacker uses the telephone
system in an attempt to scam the user into surrendering private information?
Which among the following information is not furnished by the Rules of Engagement (ROE) document?
Which among the following information is not furnished by the Rules of Engagement (ROE)
document?
Which of the following acts is a proprietary information security standard for organizations that handle cardh
Which of the following acts is a proprietary information security standard for organizations
that handle cardholder information for the major debit, credit, prepaid, e-purse, ATM, and
POS cards and applies to all entities involved in payment card processing?
Which of the following attacks is this?
An attacker injects malicious query strings in user input fields to bypass web service
authentication mechanisms and to access back-end databases. Which of the following
attacks is this?



