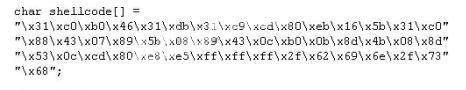What is Bob supposed to do next?
Bob is going to perform an active session hijack against Brownies Inc. He has found a target that
allows session oriented connections (Telnet) and performs the sequence prediction on the target
operating system. He manages to find an active session due to the high level of traffic on the
network. What is Bob supposed to do next?
What is this technique called?
ViruXine.W32 virus hides their presence by changing the underlying executable code. This Virus
code mutates while keeping the original algorithm intact, the code changes itself each time it runs,
but the function of the code (its semantics) will not change at all.
Here is a section of the Virus code:
What is this technique called?
"Testing the network using the same methodologies and tools employed by attackers" Identify the corr
“Testing the network using the same methodologies and tools employed by attackers” Identify the
correct terminology that defines the above statement.
what will be the result?
Nathan is testing some of his network devices. Nathan is using Macof to try and flood the ARP
cache of these switches. If these switches’ ARP cache is successfully flooded, what will be the
result?
What is the hexadecimal value of NOP instruction?
This TCP flag instructs the sending system to transmit all buffered data immediately.
This TCP flag instructs the sending system to transmit all buffered data immediately.
How would you proceed?
The network administrator at Spears Technology, Inc has configured the default gateway Cisco
router’s access-list as below:
You are hired to conduct security testing on their network. You successfully brute-force the SNMP
community string using a SNMP crack tool. The access-list configured at the router prevents you
from establishing a successful connection. You want to retrieve the Cisco configuration from the
router. How would you proceed?
How will you achieve this without raising suspicion?
You work for Acme Corporation as Sales Manager. The company has tight network security
restrictions. You are trying to steal data from the company’s Sales database (Sales.xls) and
transfer them to your home computer. Your company filters and monitors traffic that leaves from
the internal network to the Internet. How will you achieve this without raising suspicion?
"mountd access";)
Study the snort rule given below and interpret the rule.
alert tcp any any –> 192.168.1.0/24 111 (content:”|00 01 86 a5|”; msG. “mountd access”;)
What port number is used by LDAP protocol?
What port number is used by LDAP protocol?