What method of attack is best suited to crack these passwords in the shortest amount of time?
Frederickson Security Consultants is currently conducting a security audit on the networks of
Hawthorn Enterprises, a contractor for the Department of Defense. Since Hawthorn Enterprises
conducts business daily with the federal government, they must abide by very stringent security
policies. Frederickson is testing all of Hawthorn’s physical and logical security measures including
biometrics, passwords, and permissions. The federal government requires that all users must
utilize random, non-dictionary passwords that must take at least 30 days to crack. Frederickson
has confirmed that all Hawthorn employees use a random password generator for their network
passwords. The Frederickson consultants have saved off numerous SAM files from Hawthorn’s
servers using Pwdump6 and are going to try and crack the network passwords. What method of
attack is best suited to crack these passwords in the shortest amount of time?
What should you do next?
You want to know whether a packet filter is in front of 192.168.1.10. Pings to 192.168.1.10 don’t
get answered. A basic nmap scan of 192.168.1.10 seems to hang without returning any
information. What should you do next?
How would you verify if a website is authentic or not?
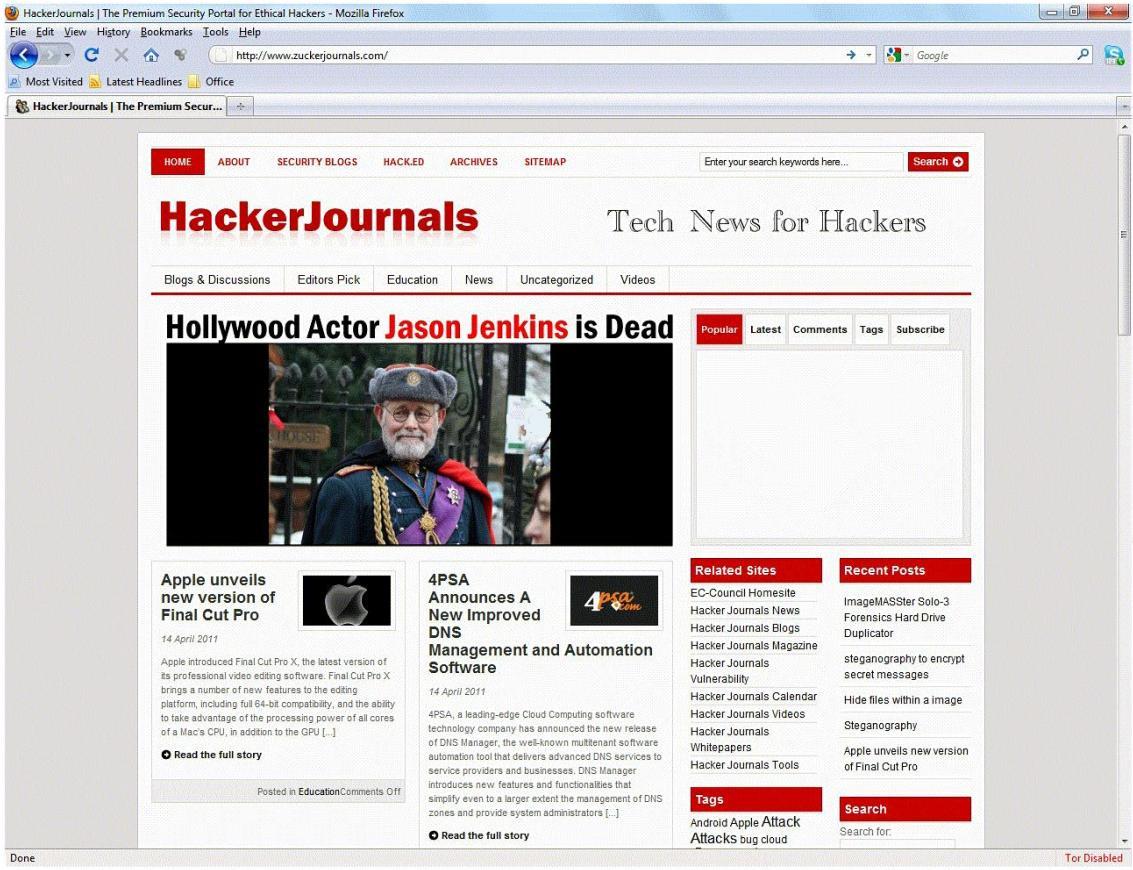
An Attacker creates a zuckerjournals.com website by copying and mirroring
HACKERJOURNALS.COM site to spread the news that Hollywood actor Jason Jenkins died in a
car accident. The attacker then submits his fake site for indexing in major search engines. When
users search for “Jason Jenkins”, attacker’s fake site shows up and dupes victims by the fake
news.
This is another great example that some people do not know what URL’s are. Real website:
Fake website: http://www.zuckerjournals.com
The website is clearly not WWW.HACKERJOURNALS.COM. It is obvious for many, but
unfortunately some people still do not know what an URL is. It’s the address that you enter into the
address bar at the top your browser and this is clearly not legit site, its www.zuckerjournals.com
How would you verify if a website is authentic or not?
A digital signature is simply a message that is encrypted with the public key instead of the private key.
A digital signature is simply a message that is encrypted with the public key instead of the private
key.
What can he infer from this kind of response?
Blane is a network security analyst for his company. From an outside IP, Blane performs an XMAS
scan using Nmap. Almost every port scanned does not illicit a response. What can he infer from
this kind of response?
what is the decimal value for XMAS scan?
In TCP communications there are 8 flags; FIN, SYN, RST, PSH, ACK, URG, ECE, CWR. These
flags have decimal numbers assigned to them:
FIN = 1
SYN = 2
RST = 4
PSH = 8
ACK = 16
URG = 32
ECE = 64
CWR =128
Example: To calculate SYN/ACK flag decimal value, add 2 (which is the decimal value of the SYN
flag) to 16 (which is the decimal value of the ACK flag), so the result would be 18.
Based on the above calculation, what is the decimal value for XMAS scan?
what does it indicate?
A simple compiler technique used by programmers is to add a terminator ‘canary word’ containing
four letters NULL (0x00), CR (0x0d), LF (0x0a) and EOF (0xff) so that most string operations are
terminated. If the canary word has been altered when the function returns, and the program
responds by emitting an intruder alert into syslog, and then halts what does it indicate?
what can an attacker do?
What type of technique might be used by these offenders to access the Internet without restriction?
Neil is closely monitoring his firewall rules and logs on a regular basis. Some of the users have
complained to Neil that there are a few employees who are visiting offensive web site during work
hours, without any consideration for others. Neil knows that he has an up-to-date content filtering
system and such access should not be authorized. What type of technique might be used by these
offenders to access the Internet without restriction?
Which of the following statement is incorrect related to this attack?
In this attack, a victim receives an e-mail claiming from PayPal stating that their account has been
disabled and confirmation is required before activation. The attackers then scam to collect not one
but two credit card numbers, ATM PIN number and other personal details.
Ignorant users usually fall prey to this scam. Which of the following statement is incorrect related
to this attack?