Which of the following provides security by implementing authentication and encryption on Wireless LAN (WLAN)?
Which of the following provides security by implementing authentication and encryption on Wireless LAN (WLAN)?
Which of the following attacks come under the category of layer 2 Denial-of-Service attacks?
Which of the following attacks come under the category of layer 2 Denial-of-Service attacks? Each correct answer represents a complete solution. Choose all that apply.
Which of the following are the three main intended goals of WEP encryption?
Which of the following are the three main intended goals of WEP encryption? Each correct answer represents a complete solution. Choose all that apply.
Which of the following protocols are required by the robust security network (RSN) for providing robust securi
Which of the following protocols are required by the robust security network (RSN) for providing robust security?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is the only IETF Standards Track based EAP method that does not provide server authenti
Which of the following is the only IETF Standards Track based EAP method that does not provide server authentication?
Which of the following steps will you take to accomplish the task?
You work as a Network Administrator for Blue Well Inc. The company has a Windows Server 2008 domain-based network. All client computers on the network run Windows Vista Ultimate. Andy, a Finance Manager, uses Windows Mail to download his e-mails to his inbox. He complains that every now and then he gets mails asking for revealing personal or financial information. He wants that such mails are not shown to him.
Which of the following steps will you take to accomplish the task?
Which of the following EAP protocols is primarily developed for third generation (3G) mobile networks?
Which of the following EAP protocols is primarily developed for third generation (3G) mobile networks?
Which of the following components splits a computer network into subnetworks in order to boost performance and
Which of the following components splits a computer network into subnetworks in order to boost performance and improve security?
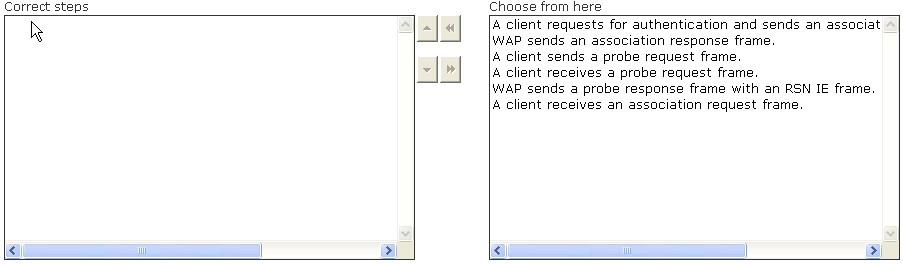
Choose the appropriate steps in the correct order to establish the communication
What security risk does this present?
A Web developer with your company wants to have wireless access for contractors that come in to work on various projects. The process of getting this approved takes time. So rather than wait, he has put his own wireless router attached to one of the network ports in his department. What security risk does this present?