The administrator should be looking for the presence of…
A trojan was recently discovered on a server. There are now concerns that there has been a security breach
that allows unauthorized people to access data. The administrator should be looking for the presence of a/an:
Which of the following has MOST likely been installed o…
During a server audit, a security administrator does not notice abnormal activity. However, a network security
analyst notices connections to unauthorized ports from outside the corporate network. Using specialized tools,
the network security analyst also notices hidden processes running. Which of the following has MOST likely
been installed on the server?
Which of the following BEST describes this type of malware?
Sara, a user, downloads a keygen to install pirated software. After running the keygen, system performance is
extremely slow and numerous antivirus alerts are displayed. Which of the following BEST describes this type of
malware?
Which of the following malware types typically allows a…
Which of the following malware types typically allows an attacker to monitor a user’s computer, is characterized
by a drive-by download, and requires no user interaction?
Which of the following is MOST likely to be contained i…
A user casually browsing the Internet is redirected to a warez site where a number of pop-ups appear. After
clicking on a pop-up to complete a survey, a drive-by download occurs. Which of the following is MOST likely to
be contained in the download?
Which of the following malware categories BEST describe…
A program has been discovered that infects a critical Windows system executable and stays dormant in
memory. When a Windows mobile phone is connected to the host, the program infects the phone’s boot loader
and continues to target additional Windows PCs or phones. Which of the following malware categories BEST
describes this program?
You must review all network logs to discover the scope of the attack…
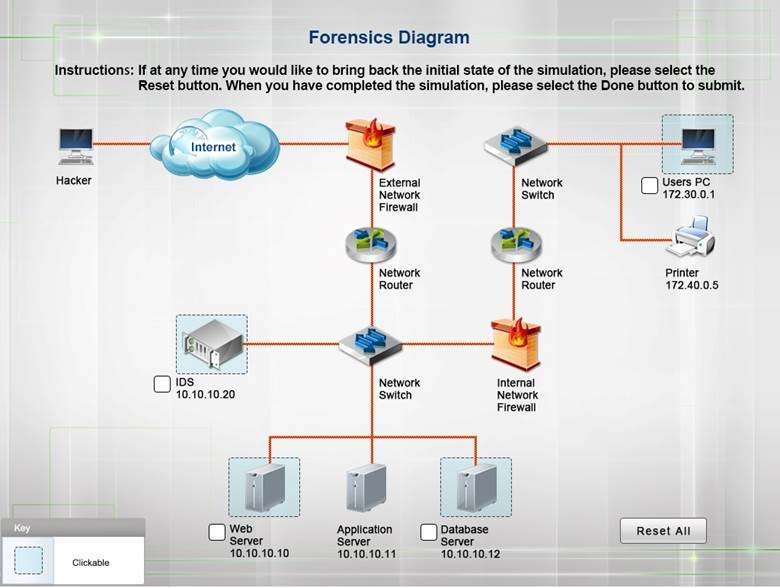
SIMULATION
A security administrator discovers that an attack has been completed against a node on the corporate network.
All available logs were collected and stored.
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have
been compromised and drag and drop the appropriate actions to complete the incident response on the
network. The environment is a critical production environment; perform the LEAST disruptive actions on the
network, while still performing the appropriate incident responses.
Instructions: The web server, database server, IDS, and User PC are clickable. Check the box of the node(s)
that have been compromised and drag and drop the appropriate actions to complete the incident response on
the network. Not all actions may be used, and order is not important. If at anytime you would like to bring back
the initial state of the simulation, please select the Reset button. When you have completed the simulation,
please select the Done button to submit. Once the simulation is submitted, please select the Next button to
continue.
Which of the following malware types may require user i…
Which of the following malware types may require user interaction, does not hide itself, and is commonly
identified by marketing pop-ups based on browsing habits?
Which of the following is the CTO concerned with?
Ann, the Chief Technology Officer (CTO), has agreed to allow users to bring their own device (BYOD) in order
to leverage mobile technology without providing every user with a company owned device. She is concernedthat users may not understand the company’s rules, and she wants to limit potential legal concerns. Which of
the following is the CTO concerned with?
Which of the following describes the disaster?
A company’s Chief Information Officer realizes the company cannot continue to operate after a disaster. Which
of the following describes the disaster?