Which of the following has MOST likely occurred?
A company provides on-demand cloud computing resources for a sensitive project. The company implements a
fully virtualized datacenter and terminal server access with two- factor authentication for customer access to the
administrative website. The security administrator at the company has uncovered a breach in data
confidentiality. Sensitive data from customer A was found on a hidden directory within the VM of company B.
Company B is not in the same industry as company A and the two are not competitors. Which of the following
has MOST
likely occurred?
which of the following type of calculations is needed?
A well-known retailer has experienced a massive credit card breach. The retailer had gone through an audit
and had been presented with a potential problem on their network. Vendors were authenticating directly to the
retailer’s AD servers, and an improper firewall rule allowed pivoting from the AD server to the DMZ where credit
card servers were kept. The firewall rule was needed for an internal application that was developed, which
presents risk. The retailer determined that because the vendors were required to have site to site VPN’s no
other security action was taken. To prove to the retailer the monetary value of this risk, which of the following
type of calculations is needed?
Drag and drop the following security controls to match the associated…
Which of the following BEST provides insight into where…
The network administrator at an enterprise reported a large data leak. One compromised server was used to
aggregate data from several critical application servers and send it out to the Internet using HTTPS. Upon
investigation, there have been no user logins over the previous week and the endpoint protection software is
not reporting any issues. Which of the following BEST provides insight into where the compromised server
collected the information?
which of the following options is MOST accurate?
A Chief Information Security Officer (CISO) has requested that a SIEM solution be implemented. The CISO
wants to know upfront what the projected TCO would be before looking further into this concern. Two vendor
proposals have been received:
Vendor A: product-based solution which can be purchased by the pharmaceutical company. Capital expenses
to cover central log collectors, correlators, storage and management consoles expected to be $150,000.
Operational expenses are expected to be a 0.5 full time employee (FTE) to manage the solution, and 1 full time
employee to respond to incidents per year.
Vendor B: managed service-based solution which can be the outsourcer for the pharmaceutical company’s
needs.
Bundled offering expected to be $100,000 per year. Operational expenses for the pharmaceutical company to
partner with the vendor are expected to be a 0.5 FTE per year.
Internal employee costs are averaged to be $80,000 per year per FTE. Based on calculating TCO of the two
vendor proposals over a 5 year period, which of the following options is MOST accurate?
Which of the following could the company view as a down…
A multi-national company has a highly mobile workforce and minimal IT infrastructure. The company utilizes a
BYOD and social media policy to integrate presence technology into global collaboration tools by individuals
and teams. As a result of the dispersed employees and frequent international travel, the company is concerned
about the safety of employees and their
families when moving in and out of certain countries. Which of the following could the company view as a
downside of using presence technology?
which of the following security activities should be pr…
A security architect has been engaged during the implementation stage of the SDLC to review a new HR
software installation for security gaps. With the project under a tight schedule to meet market commitments on
project delivery, which of the following security activities
should be prioritized by the security architect? (Select TWO).
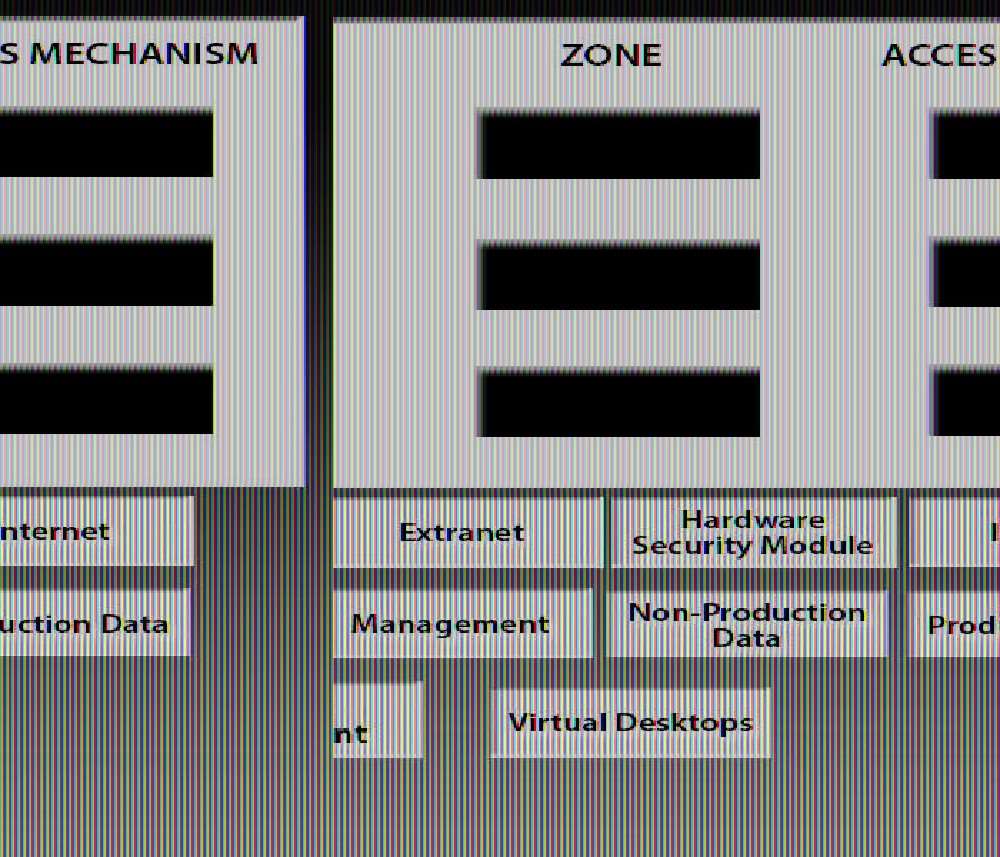
A manufacturer is planning to build a segregated network.
DRAG DROP
A manufacturer is planning to build a segregated network. There are requirements to segregate development
and test infrastructure from production and the need to support multiple entry points into the network depending
on the service being accessed. There are also strict rules in place to only permit user access from within the
same zone. Currently, the following access requirements have been identified:
1. Developers have the ability to perform technical validation of development applications.
2. End users have the ability to access internal web applications.
3. Third-party vendors have the ability to support applications. In order to meet segregation and access
requirements, drag and drop the appropriate network zone that the user would be accessing and the access
mechanism to meet the above criteria. Options may be used once or not at all. All placeholders must be filled.
Which of the following security assessment methods are …
The following has been discovered in an internally developed application: Error – Memory allocated but not
freed: char *myBuffer = malloc(BUFFER_SIZE); if (myBuffer != NULL) { *myBuffer =
STRING_WELCOME_MESSAGE; printf(“Welcome to: %s\\n”, myBuffer); } exit(0);
Which of the following security assessment methods are likely to reveal this security weakness? (Select TWO).
Company A has experienced external attacks on their network…
DRAG DROP
Company A has experienced external attacks on their network and wants to minimize the attacks from
reoccurring. Modify the network diagram to prevent SQL injections, XSS attacks, smurf attacks, e-mail spam,
downloaded malware, viruses and ping attacks. The company can spend a MAXIMUM of $50,000 USD. A cost
list for each item is listed below:
1. Anti-Virus Server – $10,000
2. Firewall-$15,000
3. Load Balanced Server – $10,000 4. NIDS/NIPS-$10,000
5. Packet Analyzer – $5,000
6. Patch Server-$15,000
7. Proxy Server-$20,000 8. Router-$10,000
9. Spam Filter-$5,000
10. Traffic Shaper – $20,000
11. Web Application Firewall – $10,000
Instructions: Not all placeholders in the diagram need to be filled and items can only be used once. If you place
an object on the network diagram, you can remove it by clicking the (x) in the upper right-hand of the object.