Which of the following sections of the proposal would b…
A project manager is evaluating proposals for a cloud computing project. The project manager is particularly concerned about logical security controls in place at
the service provider’s facility. Which of the following sections of the proposal would be MOST important to review, given the project manager’s concerns?
Which of the following processes can the administrator …
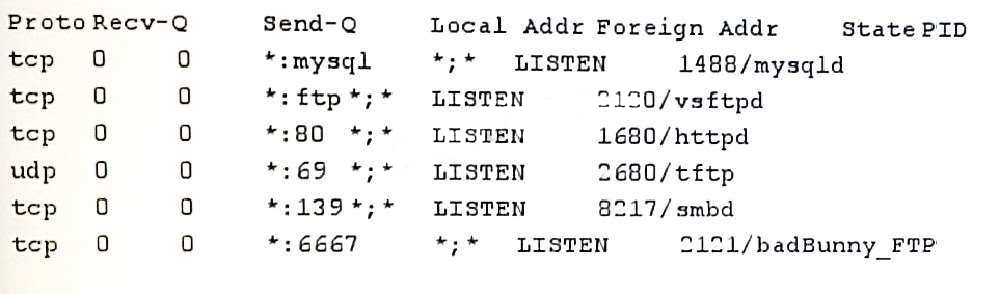
An administrator is hardening systems and wants to disable unnecessary services. One Linux server hosts files used by a Windows web server on another
machine. The Linux server is only used for secure file transfer, but requires a share for the Windows web server as well. The administrator sees the following output
from a netstat -1p command:
Which of the following processes can the administrator kill without risking impact to the purpose and function of the Linux or Windows servers? (Select Three)
Which of the following can be implemented to provide sy…
A new employee has been hired to perform system administration duties across a large enterprise comprised of multiple separate security domains. Each remote
location implements a separate security domain. The new employee has successfully responded to and fixed computer issues for the main office. When the new
employee tries to perform work on remote computers, the following messages appears. You need permission to perform this action. Which of the following can be
implemented to provide system administrators with the ability to perform administrative tasks on remote computers using their uniquely assigned account?
which of the following system components FIRST?
A security administrator working for a law enforcement organization is asked to secure a computer system at the scene of a crime for transport to the law
enforcement forensic facility. In order to capture as mush evidence as possible, the computer system has been left running. The security administrator begins
information by image which of the following system components FIRST?
Which of the following options is MOST likely the cause…
A system administrator runs a network inventory scan every Friday at 10:00 am to track the progress of a large organization’s operating system upgrade of all
laptops. The system administrator discovers that some laptops are now only being reported as IP addresses. Which of the following options is MOST likely the
cause of this issue?
Which of the following policies should be enforced to p…
A recent review of accounts on various systems has found that after employees passwords are required to change they are recycling the same password as before.
Which of the following policies should be enforced to prevent this from happening? (Select TWO)
which of the following is the MOST influential concern …
When implementing a mobile security strategy for an organization which of the following is the MOST influential concern that contributes to that organization’s ability
to extend enterprise policies to mobile devices?
Which of the following will help mitigate the risk in t…
A company must send sensitive data over a non-secure network via web services. The company suspects that competitors are actively trying to intercept all
transmissions. Some of the information may be valuable to competitors, even years after it has been sent. Which of the following will help mitigate the risk in the
scenario?
Which of the following MUST be configured on the switch…
An administrator wants to configure a switch port so that it separates voice and data traffic. Which of the following MUST be configured on the switch port to enforce
separation of traffic?
Which of the following attack mechanisms can the attack…
While performing surveillance activities an attacker determines that an organization is using 802.1X to secure LAN access. Which of the following attack
mechanisms can the attacker utilize to bypass the identified network security controls?