Which of the following would be the BEST place to start?
An administrator would like to review the effectiveness of existing security in the enterprise. Which
of the following would be the BEST place to start?
Which of the following should be implemented to secure the devices without risking availability?
A company has proprietary mission critical devices connected to their network which are
configured remotely by both employees and approved customers. The administrator wants to
monitor device security without changing their baseline configuration. Which of the following
should be implemented to secure the devices without risking availability?
Which of the following should be implemented to secure the devices without risking availability?
A company has proprietary mission critical devices connected to their network which are
configured remotely by both employees and approved customers. The administrator wants to
monitor device security without changing their baseline configuration. Which of the following
should be implemented to secure the devices without risking availability?
Which of the following firewall rules only denies DNS zone transfers?
Which of the following firewall rules only denies DNS zone transfers?
Configure the firewall to allow these four rules.
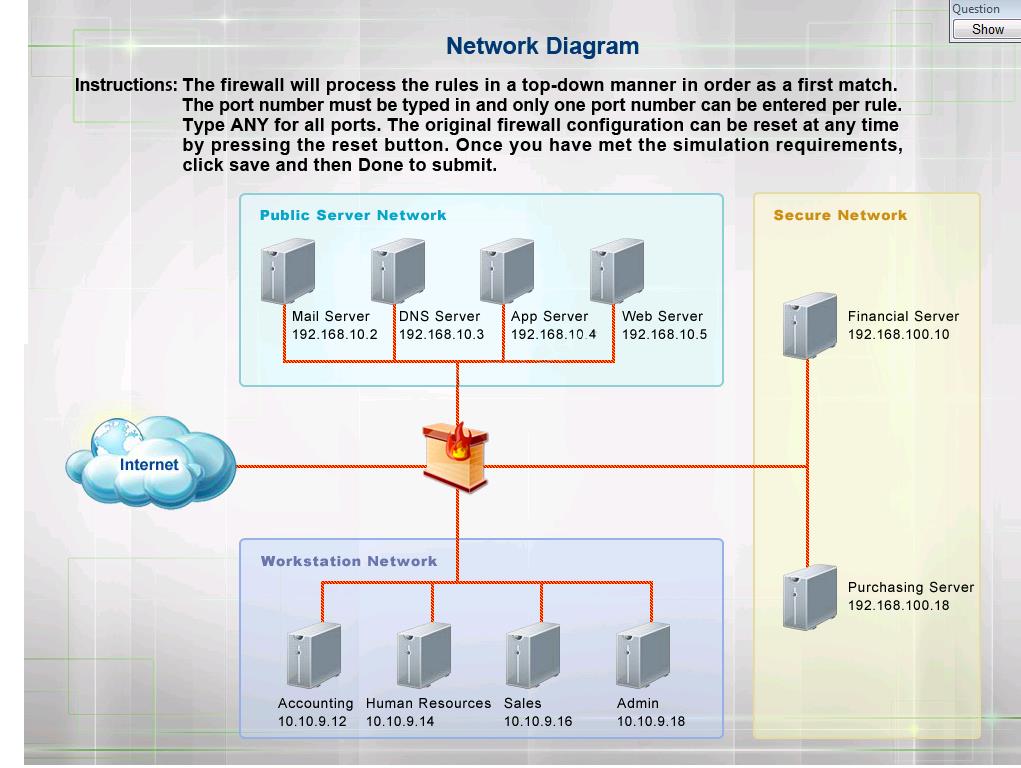
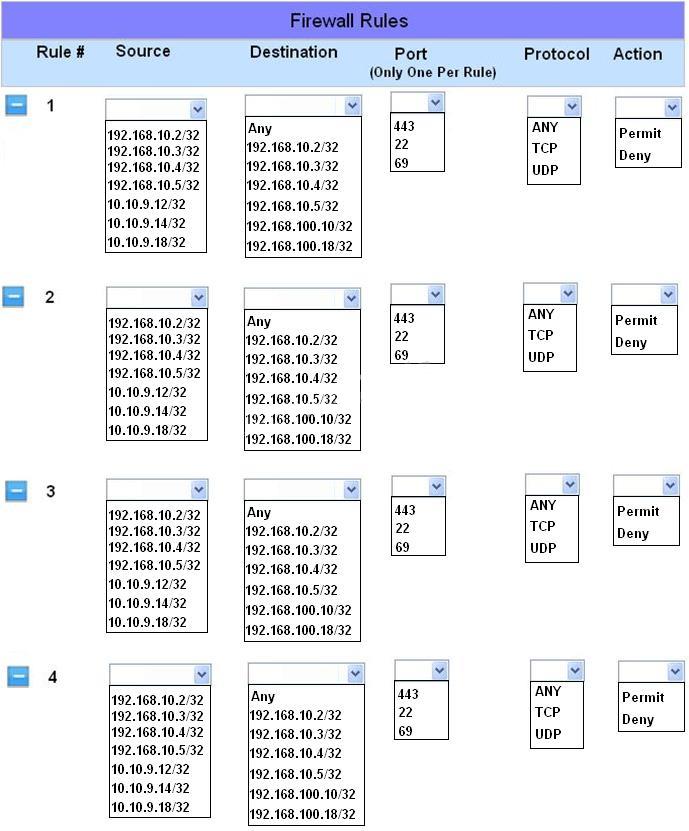
The security administrator has installed a new firewall which implements an implicit DENY policy by default.
HOTSPOT
The security administrator has installed a new firewall which implements an implicit DENY policy
by default. Click on the firewall and configure it to allow ONLY the following communication.
1. The Accounting workstation can ONLY access the web server on the public network over the
default HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over
the default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure network over
the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The
port number must be typed in and only one port number can be entered per rule Type ANY for all
ports. The original firewall configuration can be reset at any time by pressing the reset button.
Once you have met the simulation requirements, click save and then Done to submit.
Which of the following firewall rules only denies DNS zone transfers?
Which of the following firewall rules only denies DNS zone transfers?
Which of the following would accomplish this task?
A security administrator suspects that an increase in the amount of TFTP traffic on the network is
due to unauthorized file transfers, and wants to configure a firewall to block all TFTP traffic.
Which of the following would accomplish this task?
How could Sara BEST accommodate the vendor?
NO: 36
Sara, a security technician, has received notice that a vendor coming in for a presentation will
require access to a server outside of the network. Currently, users are only able to access remote
sites through a VPN connection. How could Sara BEST accommodate the vendor?
Which of the following should be recommended to isolate the VMs from one another?
A technician is deploying virtual machines for multiple customers on a single physical host to
reduce power consumption in a data center. Which of the following should be recommended to
isolate the VMs from one another?