Which of the following should the technician implement to meet managements request?
A technician is reviewing the logical access control method an organization uses. One of the senior
managers requests that the technician prevent staff members from logging on during nonworking days.
Which of the following should the technician implement to meet managements request?
Which of the following should be implemented in order to compliment password usage and smart cards?
Ann, the security administrator, wishes to implement multifactor security. Which of the following should
be implemented in order to compliment password usage and smart cards?
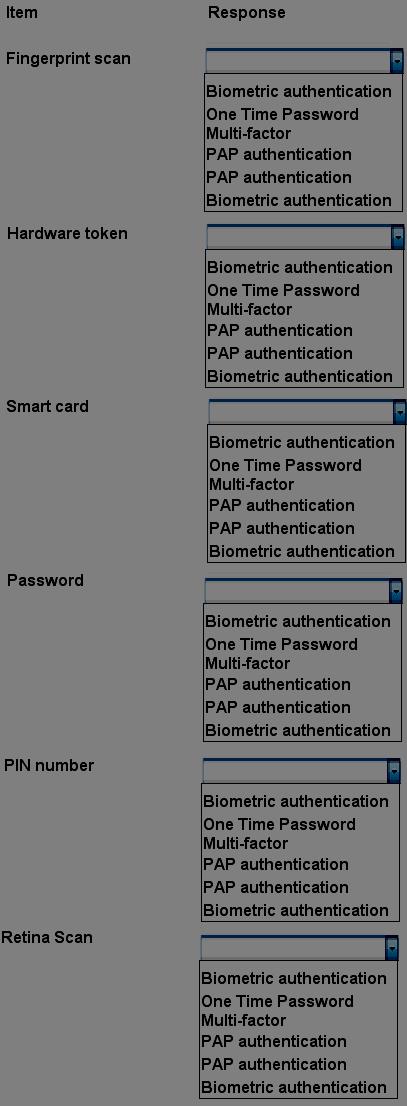
Select the appropriate authentication type for the following items:
which of the following?
A network administrator uses an RFID card to enter the datacenter, a key to open the server rack, and a
username and password to logon to a server. These are examples of which of the following?
which of the following attacks?
Use of a smart card to authenticate remote servers remains MOST susceptible to which of the following
attacks?
Which of the following describes this access control type?
Employee badges are encoded with a private encryption key and specific personal information.
The encoding is then used to provide access to the network. Which of the following describes this access
control type?
Which of the following would fulfill the CISO’s requirements?
A Chief Information Security Officer (CISO) wants to implement two-factor authentication within the
company. Which of the following would fulfill the CISO’s requirements?
Which of the following should be implemented during the authorization stage?
A technician wants to implement a dual factor authentication system that will enable the organization to
authorize access to sensitive systems on a need-to-know basis. Which of the following should be
implemented during the authorization stage?
Which of the following is an example of multifactor authentication?
Which of the following is an example of multifactor authentication?
Which of the following protocols provides for mutual authentication of the client and server?
Which of the following protocols provides for mutual authentication of the client and server?