Which of the following malware types is MOST likely to execute its payload after Jane, an employee, has left t
Which of the following malware types is MOST likely to execute its payload after Jane, an employee, has
left the company?
Which of the following explains the difference between these two types of malware?
Pete, a security analyst, has been tasked with explaining the different types of malware to his colleagues.
The two malware types that the group seems to be most interested in are botnets and viruses. Which of
the following explains the difference between these two types of malware?
Which of the following types of malware is on Ann’s workstation?
A user, Ann, is reporting to the company IT support group that her workstation screen is blank other than
a window with a message requesting payment or else her hard drive will be formatted. Which of the
following types of malware is on Ann’s workstation?
which is difficult to reverse engineer in a virtual lab?
Which of the following describes a type of malware which is difficult to reverse engineer in a virtual lab?
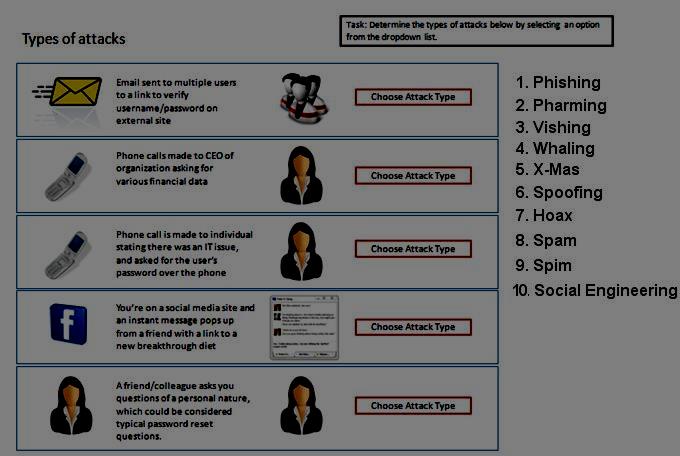
Select the appropriate attack from each drop down list to label the corresponding…
Determine the types of Attacks from right to specific action.
Which of the following attacks is occurring?
A server with the IP address of 10.10.2.4 has been having intermittent connection issues. The logs show
repeated connection attempts from the following IPs:
10.10.3.16
10.10.3.23
212.178.24.26
217.24.94.83
These attempts are overloading the server to the point that it cannot respond to traffic. Which of the
following attacks is occurring?
A distributed denial of service attack can BEST be described as:
A distributed denial of service attack can BEST be described as:
The administrator suspects that:
An administrator notices an unusual spike in network traffic from many sources. The administrator
suspects that:
Which of the following will BEST mitigate the risk if implemented on the switches?
A security technician at a small business is worried about the Layer 2 switches in the network suffering
from a DoS style attack caused by staff incorrectly cabling network connections between switches.
Which of the following will BEST mitigate the risk if implemented on the switches?