Which of the following explains this scenario?
A consultant has been tasked to assess a client’s network. The client reports frequent network outages.
Upon viewing the spanning tree configuration, the consultant notices that an old and law performing
edge switch on the network has been elected to be the root bridge. Which of the following explains this
scenario?
The access control method that BEST satisfies these objectives is:
An organization is trying to decide which type of access control is most appropriate for the network. The
current access control approach is too complex and requires significant overhead. Management would
like to simplify the access control and provide user with the ability to determine what permissions should
be applied to files, document, and directories. The access control method that BEST satisfies these
objectives is:
Which of the following password requirements will MOST effectively improve the security posture of the applica
While reviewing the security controls in place for a web-based application, a security controls assessor
notices that there are no password strength requirements in place. Because of this vulnerability,
passwords might be easily discovered using a brute force attack. Which of the following password
requirements will MOST effectively improve the security posture of the application against these attacks?
(Select two)
Which of the following should the administrator do to prevent all unapproved software from running on the user
A security administrator determined that users within the company are installing unapproved software.
Company policy dictates that only certain applications may be installed or ran on the user’s computers
without exception. Which of the following should the administrator do to prevent all unapproved
software from running on the user’s computer?
Which of the following configuration commands should be implemented to enforce this requirement?
A security administrator is tasked with implementing centralized management of all network devices.
Network administrators will be required to logon to network devices using their LDAP credentials. All
command executed by network administrators on network devices must fall within a preset list of
authorized commands and must be logged to a central facility. Which of the following configuration
commands should be implemented to enforce this requirement?
Which of the following methods has MOST likely been used?
A website administrator has received an alert from an application designed to check the integrity of the
company’s website. The alert indicated that the hash value for a particular MPEG file has changed. Upon
further investigation, the media appears to be the same as it was before the alert. Which of the following
methods has MOST likely been used?
This is because the encryption scheme in use adheres to:
An attacker captures the encrypted communication between two parties for a week, but is unable to
decrypt the messages. The attacker then compromises the session key during one exchange and
successfully compromises a single message. The attacker plans to use this key to decrypt previously
captured and future communications, but is unable to. This is because the encryption scheme in use
adheres to:
hown below: From IT department To employeeSubject email quota exceeded Pease click on the following link http:
Many employees are receiving email messages similar to the one shown below:
From IT department
To employeeSubject email quota exceeded
Pease click on the following link http:www.website.info/email.php?quota=1Gb and provide your
username and password to increase your email quota. Upon reviewing other similar emails, the security
administrator realized that all the phishing URLs have the following common elements; they all use HTTP,
they all come from .info domains, and they all contain the same URI.
Which of the following should the security administrator configure on the corporate content filter to
prevent users from accessing the phishing URL, while at the same time minimizing false positives?
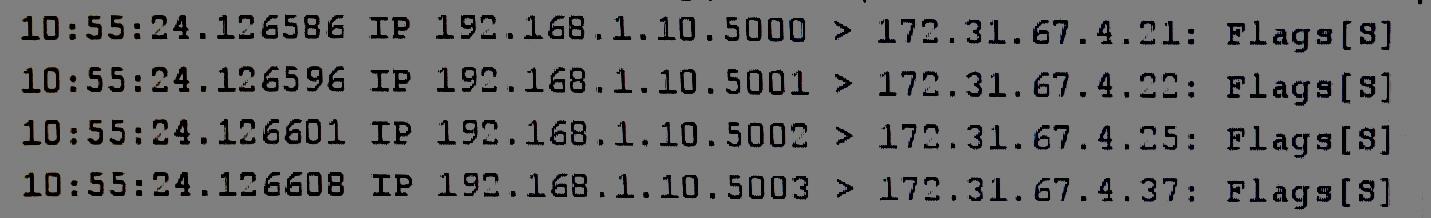
Which of the following ACLs provides the BEST protection against the above attack and any further attacks from
Which of the following would provide the BEST solution?
The IT department needs to prevent users from installing untested applications. Which of the following
would provide the BEST solution?